1. Overview
The Encap REST API is used to integrate client systems with the Encap server in order to perform mobile authentication of customers via designated mobile applications that integrate the Encap mobile authentication API.
Operations provided via the API are currently divided into the following categories:
-
Enrollment: Operations facilitating the enrollment of a supported application instance on a customer’s mobile device with the Encap server. The enrollment process creates a very strong cryptographic binding between the device/application instance and the server which can then be used to perform authentication operations.
-
Authentication: Operations for executing secure mobile authentication requests via previously-enrolled device/application instances.
-
Device Management: Operations for the management of enrolled device/application instances, including locking/unlocking of instances and deactivation/un-enrollment.
-
Admin APIs: Administrative checks and operations.
2. Common concepts
2.1. REST API authentication
Authentication for REST API calls (not to confuse with the authentication service itself) are handled by using Basic Authentication. All requests are required to have an Authorization header containing a Basic Authentication string. The Basic Authentication should have the API key id as username and the API key secret as password. API key provisioning is handled by the Encap server administrator.
GET /api/smart-device/v1/authentications/5a95de3c-98c9-4de9-9bb5-83931fd2594c HTTP/1.1
Authorization: Basic OGVmNmRiNjQtMzU0NS00Yjk0LTkxOTQtM2UwODgzNDAwM2I2OkFBQUFBQUFBQUFBQUFBQUFBQUFBQUE9PQ==
Host: localhost:80802.1.1. Authentication error response
During authentication there are two errors that can occur
400 Bad Request is returned if the request is missing the required authentication headers.
401 Unauthorized is returned when authentication fails due to wrong/invalid API key id or API key secret.
2.2. HTTP verbs
The API is implemented to adhere as closely as possible to HTTP standard and REST conventions in its use of HTTP verbs.
| Verb | Usage |
|---|---|
|
Used to retrieve a resource. |
|
Used to create a new resource. |
|
Full update of an existing resource. |
|
Partial update of an existing resource. |
|
Used to delete an existing resource. |
2.3. HTTP status codes
The API is implemented to adhere as closely as possible to HTTP standard and REST conventions in its use of HTTP status codes.
| Status code | Usage |
|---|---|
|
The request completed successfully |
|
A new resource has been created successfully. The resource’s URI is available from the response’s
|
|
An update to an existing resource has been applied successfully |
|
The request was malformed. The response body will include an error providing further information. |
|
Authentication/Authorization failed for the request |
|
Client not authorized to access the operation on the specified resource |
|
Resource with the given id does not exist |
|
Tried to create a resource that already exists |
|
Conditional request, but conditions not fulfilled |
|
Content well formed but content validation failed |
|
Conditional request required but no condition given |
|
Unexpected failure on server side |
2.4. Errors
The API uses HTTP status codes to indicate the success or failure of an API request. In general, codes in the 2xx range indicate success, codes in the 4xx range indicate an error that failed given the request data provided (e.g., a required parameter was omitted, a device state not appropriate, etc.), and codes in the 5xx range indicate an error with the API servers.
Not all errors map cleanly onto HTTP response codes. Some 4xx codes also contain an error entity in the response explaining the error in more detail. In very rare cases HTTP 500 will do the same.
2.4.1. The error object
The error entity has the following response structure:
| Field | Type | Description |
|---|---|---|
|
|
Holds a duplicate copy of the HTTP error status code for convenience, so that clients can “see” it without having to analyze the response’s header |
|
|
Unique code for this specific error type. More fine grained than the HTTP code, e.g. "AUTH_LEVEL_NOT_AVAILABLE_FOR_DEVICE" |
|
|
Short description of the error, what might have cause it and possibly a “fixing” proposal, e.g. "Device is not activated for 2FA authentication, activate the device for 2FA before trying to use it for 2FA authentication" |
|
|
The correlation ID sent in the request or generated on the server. Will contain the same value as the response header X-Correlation-UUID. Can be used to find the correlating error messages from the server log |
|
|
Detailed message, containing additional data that might be relevant to the developer. Only provided when development mode is switched on and can potentially contain stack trace information or similar |
|
|
Array of field specific errors if there are any, typically used for validation faults (HTTP 422) |
Field specific error
| Field | Type | Description |
|---|---|---|
|
|
Field name if the error is related to a specific field |
|
|
Specific code for the error situation, e.g. "FIELD_TO_LONG" |
|
|
Human readable description of the error code, e.g. "Field allows max 255 characters" |
2.4.2. Error codes
| Error code | Description |
|---|---|
|
An unexpected error occurred |
|
Validation of request failed |
|
Resource does not exist |
|
Resource already exists |
|
Provided offset id does not exist |
|
Server was not able to parse the request |
|
Provided media type is not supported, server supports application/json |
|
Server does not accept the request |
|
Request is unauthorized |
|
Device is not registered |
|
Provided session expiry time exceeds the maximum allowed value |
|
Too many concurrent active activation sessions |
|
Server failed to create activation code |
|
No active sessions found for the device |
|
Device is locked. See device API for details |
|
Device is not locked |
|
Provided session is not an activation session |
|
Authentication level is not allowed |
|
Authentication method is not configured for this app config |
|
Authentication method and level does not match each other |
|
Authentication method is not activated for the device |
|
Provided session is not an authentication session |
|
Provided session is not an offline authentication session |
|
The purpose of the provided session is not supported |
|
The application configuration provided is not valid. |
|
The application ID was not found. |
|
The APNS key is used by one or more application configurations |
|
The End-to-End key has status ENABLED and is considered in use |
|
The patch request is not of a valid format and cannot be mapped to the object that is supposed to be updated. |
|
Authentication request has sendPush flag set to true, but nativePushEnabled option in app configuration is false. |
|
The session has expired and can no longer be used |
|
The session has already had a failed or successful outcome |
|
The session is cancelled and can no longer be used |
|
The specified authentication method is locked. If the method in question is an offline-method, other methods might still work. |
|
The authentication method you are trying to unlock is not locked |
|
Authentication method is required in the request |
|
The request is missing one or more request parameters |
|
The purpose of the given session is not perform recovery. |
|
Too many device IDs were passed when listing sessions for devices; the number of devices is limited to 100. |
|
Failed to delete face authentication method of device due to Server Side Face Adapter error or unavailability. |
Example request
A request that triggers a validation error will produce a
422 Unprocessable Entity response:
HTTP/1.1 422 Unprocessable Entity
X-Correlation-UUID: 3bdab914-b37a-408a-acaa-984e0c8503fc
Content-Type: application/json
Content-Length: 14100
{
"status" : 422,
"code" : "REST_VALIDATION_FAULT",
"message" : "Parameter validation failed on request /smart-device/v1/devices/0ff1a0c4-5a2b-4711-b4d6-50828f0824ed/sessions. For more information see field specific errors.",
"correlation_id" : "3bdab914-b37a-408a-acaa-984e0c8503fc",
"errors" : [ {
"field" : "limit",
"code" : "REST_TYPE_MISMATCH",
"message" : "Failed to convert property value of type 'java.lang.String' to required type 'int' for property 'limit'; For input string: \"pp\""
}, {
"field" : "offset",
"code" : "REST_TYPE_MISMATCH",
"message" : "Failed to convert property value of type 'java.lang.String' to required type 'java.util.UUID' for property 'offset'; Invalid UUID string: ll"
} ],
"developer_message" : "Validation failed for argument [2] in org.springframework.http.ResponseEntity<com.encapsecurity.encap.rest.api.dto.PaginationResponseDTO<com.encapsecurity.encap.rest.api.dto.DeviceSessionDetailsDTO>> com.encapsecurity.encap.rest.controller.DeviceController.getSessionsForDevice(com.encapsecurity.encap.domain.EncapPrincipal,java.util.UUID,com.encapsecurity.encap.rest.api.dto.PaginationRequestDTO) with 2 errors: [Field error in object 'paginationRequestDTO' on field 'limit': rejected value [pp]; codes [typeMismatch.paginationRequestDTO.limit,typeMismatch.limit,typeMismatch.int,typeMismatch]; arguments [org.springframework.context.support.DefaultMessageSourceResolvable: codes [paginationRequestDTO.limit,limit]; arguments []; default message [limit]]; default message [Failed to convert property value of type 'java.lang.String' to required type 'int' for property 'limit'; For input string: \"pp\"]] [Field error in object 'paginationRequestDTO' on field 'offset': rejected value [ll]; codes [typeMismatch.paginationRequestDTO.offset,typeMismatch.offset,typeMismatch.java.util.UUID,typeMismatch]; arguments [org.springframework.context.support.DefaultMessageSourceResolvable: codes [paginationRequestDTO.offset,offset]; arguments []; default message [offset]]; default message [Failed to convert property value of type 'java.lang.String' to required type 'java.util.UUID' for property 'offset'; Invalid UUID string: ll]] \norg.springframework.web.bind.MethodArgumentNotValidException: Validation failed for argument [2] in org.springframework.http.ResponseEntity<com.encapsecurity.encap.rest.api.dto.PaginationResponseDTO<com.encapsecurity.encap.rest.api.dto.DeviceSessionDetailsDTO>> com.encapsecurity.encap.rest.controller.DeviceController.getSessionsForDevice(com.encapsecurity.encap.domain.EncapPrincipal,java.util.UUID,com.encapsecurity.encap.rest.api.dto.PaginationRequestDTO) with 2 errors: [Field error in object 'paginationRequestDTO' on field 'limit': rejected value [pp]; codes [typeMismatch.paginationRequestDTO.limit,typeMismatch.limit,typeMismatch.int,typeMismatch]; arguments [org.springframework.context.support.DefaultMessageSourceResolvable: codes [paginationRequestDTO.limit,limit]; arguments []; default message [limit]]; default message [Failed to convert property value of type 'java.lang.String' to required type 'int' for property 'limit'; For input string: \"pp\"]] [Field error in object 'paginationRequestDTO' on field 'offset': rejected value [ll]; codes [typeMismatch.paginationRequestDTO.offset,typeMismatch.offset,typeMismatch.java.util.UUID,typeMismatch]; arguments [org.springframework.context.support.DefaultMessageSourceResolvable: codes [paginationRequestDTO.offset,offset]; arguments []; default message [offset]]; default message [Failed to convert property value of type 'java.lang.String' to required type 'java.util.UUID' for property 'offset'; Invalid UUID string: ll]] \n\tat org.springframework.web.method.annotation.ModelAttributeMethodProcessor.resolveArgument(ModelAttributeMethodProcessor.java:158)\n\tat org.springframework.web.method.support.HandlerMethodArgumentResolverComposite.resolveArgument(HandlerMethodArgumentResolverComposite.java:122)\n\tat org.springframework.web.method.support.InvocableHandlerMethod.getMethodArgumentValues(InvocableHandlerMethod.java:227)\n\tat org.springframework.web.method.support.InvocableHandlerMethod.invokeForRequest(InvocableHandlerMethod.java:181)\n\tat org.springframework.web.servlet.mvc.method.annotation.ServletInvocableHandlerMethod.invokeAndHandle(ServletInvocableHandlerMethod.java:118)\n\tat org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerAdapter.invokeHandlerMethod(RequestMappingHandlerAdapter.java:991)\n\tat org.springframework.web.servlet.mvc.method.annotation.RequestMappingHandlerAdapter.handleInternal(RequestMappingHandlerAdapter.java:896)\n\tat org.springframework.web.servlet.mvc.method.AbstractHandlerMethodAdapter.handle(AbstractHandlerMethodAdapter.java:87)\n\tat org.springframework.web.servlet.DispatcherServlet.doDispatch(DispatcherServlet.java:1089)\n\tat org.springframework.web.servlet.DispatcherServlet.doService(DispatcherServlet.java:979)\n\tat org.springframework.web.servlet.FrameworkServlet.processRequest(FrameworkServlet.java:1014)\n\tat org.springframework.web.servlet.FrameworkServlet.doGet(FrameworkServlet.java:903)\n\tat jakarta.servlet.http.HttpServlet.service(HttpServlet.java:633)\n\tat org.springframework.web.servlet.FrameworkServlet.service(FrameworkServlet.java:885)\n\tat org.springframework.test.web.servlet.TestDispatcherServlet.service(TestDispatcherServlet.java:72)\n\tat jakarta.servlet.http.HttpServlet.service(HttpServlet.java:723)\n\tat org.springframework.mock.web.MockFilterChain$ServletFilterProxy.doFilter(MockFilterChain.java:165)\n\tat org.springframework.mock.web.MockFilterChain.doFilter(MockFilterChain.java:132)\n\tat com.encapsecurity.encap.rest.filter.BasicAuthenticationFilter.doFilterInternal(BasicAuthenticationFilter.java:89)\n\tat org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:116)\n\tat org.springframework.mock.web.MockFilterChain.doFilter(MockFilterChain.java:132)\n\tat com.encapsecurity.encap.rest.filter.RequestCorrelationIdFilter.doFilterInternal(RequestCorrelationIdFilter.java:21)\n\tat org.springframework.web.filter.OncePerRequestFilter.doFilter(OncePerRequestFilter.java:116)\n\tat org.springframework.mock.web.MockFilterChain.doFilter(MockFilterChain.java:132)\n\tat com.encapsecurity.encap.config.filter.RequestContextFilter.doFilter(RequestContextFilter.java:83)\n\tat org.springframework.mock.web.MockFilterChain.doFilter(MockFilterChain.java:132)\n\tat org.springframework.test.web.servlet.MockMvc.perform(MockMvc.java:201)\n\tat com.encapsecurity.encap.rest.controller.ExceptionThrowingControllerTest.typeMismatchOnPaginationRequestParam(ExceptionThrowingControllerTest.java:111)\n\tat java.base/jdk.internal.reflect.DirectMethodHandleAccessor.invoke(DirectMethodHandleAccessor.java:103)\n\tat java.base/java.lang.reflect.Method.invoke(Method.java:580)\n\tat org.junit.platform.commons.util.ReflectionUtils.invokeMethod(ReflectionUtils.java:775)\n\tat org.junit.platform.commons.support.ReflectionSupport.invokeMethod(ReflectionSupport.java:479)\n\tat org.junit.jupiter.engine.execution.MethodInvocation.proceed(MethodInvocation.java:60)\n\tat org.junit.jupiter.engine.execution.InvocationInterceptorChain$ValidatingInvocation.proceed(InvocationInterceptorChain.java:131)\n\tat org.junit.jupiter.engine.extension.TimeoutExtension.intercept(TimeoutExtension.java:161)\n\tat org.junit.jupiter.engine.extension.TimeoutExtension.interceptTestableMethod(TimeoutExtension.java:152)\n\tat org.junit.jupiter.engine.extension.TimeoutExtension.interceptTestMethod(TimeoutExtension.java:91)\n\tat org.junit.jupiter.engine.execution.InterceptingExecutableInvoker$ReflectiveInterceptorCall.lambda$ofVoidMethod$0(InterceptingExecutableInvoker.java:112)\n\tat org.junit.jupiter.engine.execution.InterceptingExecutableInvoker.lambda$invoke$0(InterceptingExecutableInvoker.java:94)\n\tat org.junit.jupiter.engine.execution.InvocationInterceptorChain$InterceptedInvocation.proceed(InvocationInterceptorChain.java:106)\n\tat org.junit.jupiter.engine.execution.InvocationInterceptorChain.proceed(InvocationInterceptorChain.java:64)\n\tat org.junit.jupiter.engine.execution.InvocationInterceptorChain.chainAndInvoke(InvocationInterceptorChain.java:45)\n\tat org.junit.jupiter.engine.execution.InvocationInterceptorChain.invoke(InvocationInterceptorChain.java:37)\n\tat org.junit.jupiter.engine.execution.InterceptingExecutableInvoker.invoke(InterceptingExecutableInvoker.java:93)\n\tat org.junit.jupiter.engine.execution.InterceptingExecutableInvoker.invoke(InterceptingExecutableInvoker.java:87)\n\tat org.junit.jupiter.engine.descriptor.TestMethodTestDescriptor.lambda$invokeTestMethod$7(TestMethodTestDescriptor.java:216)\n\tat org.junit.platform.engine.support.hierarchical.ThrowableCollector.execute(ThrowableCollector.java:73)\n\tat org.junit.jupiter.engine.descriptor.TestMethodTestDescriptor.invokeTestMethod(TestMethodTestDescriptor.java:212)\n\tat org.junit.jupiter.engine.descriptor.TestMethodTestDescriptor.execute(TestMethodTestDescriptor.java:137)\n\tat org.junit.jupiter.engine.descriptor.TestMethodTestDescriptor.execute(TestMethodTestDescriptor.java:69)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.lambda$executeRecursively$6(NodeTestTask.java:156)\n\tat org.junit.platform.engine.support.hierarchical.ThrowableCollector.execute(ThrowableCollector.java:73)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.lambda$executeRecursively$8(NodeTestTask.java:146)\n\tat org.junit.platform.engine.support.hierarchical.Node.around(Node.java:137)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.lambda$executeRecursively$9(NodeTestTask.java:144)\n\tat org.junit.platform.engine.support.hierarchical.ThrowableCollector.execute(ThrowableCollector.java:73)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.executeRecursively(NodeTestTask.java:143)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.execute(NodeTestTask.java:100)\n\tat org.junit.platform.engine.support.hierarchical.ForkJoinPoolHierarchicalTestExecutorService$ExclusiveTask.exec(ForkJoinPoolHierarchicalTestExecutorService.java:274)\n\tat java.base/java.util.concurrent.ForkJoinTask.doExec(ForkJoinTask.java:387)\n\tat java.base/java.util.concurrent.ForkJoinPool$WorkQueue.tryRemoveAndExec(ForkJoinPool.java:1351)\n\tat java.base/java.util.concurrent.ForkJoinTask.awaitDone(ForkJoinTask.java:422)\n\tat java.base/java.util.concurrent.ForkJoinTask.join(ForkJoinTask.java:651)\n\tat org.junit.platform.engine.support.hierarchical.ForkJoinPoolHierarchicalTestExecutorService.joinConcurrentTasksInReverseOrderToEnableWorkStealing(ForkJoinPoolHierarchicalTestExecutorService.java:201)\n\tat org.junit.platform.engine.support.hierarchical.ForkJoinPoolHierarchicalTestExecutorService.invokeAll(ForkJoinPoolHierarchicalTestExecutorService.java:167)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.lambda$executeRecursively$6(NodeTestTask.java:160)\n\tat org.junit.platform.engine.support.hierarchical.ThrowableCollector.execute(ThrowableCollector.java:73)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.lambda$executeRecursively$8(NodeTestTask.java:146)\n\tat org.junit.platform.engine.support.hierarchical.Node.around(Node.java:137)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.lambda$executeRecursively$9(NodeTestTask.java:144)\n\tat org.junit.platform.engine.support.hierarchical.ThrowableCollector.execute(ThrowableCollector.java:73)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.executeRecursively(NodeTestTask.java:143)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.execute(NodeTestTask.java:100)\n\tat org.junit.platform.engine.support.hierarchical.ForkJoinPoolHierarchicalTestExecutorService$ExclusiveTask.exec(ForkJoinPoolHierarchicalTestExecutorService.java:274)\n\tat java.base/java.util.concurrent.ForkJoinTask.doExec(ForkJoinTask.java:387)\n\tat java.base/java.util.concurrent.ForkJoinPool$WorkQueue.tryRemoveAndExec(ForkJoinPool.java:1351)\n\tat java.base/java.util.concurrent.ForkJoinTask.awaitDone(ForkJoinTask.java:422)\n\tat java.base/java.util.concurrent.ForkJoinTask.join(ForkJoinTask.java:651)\n\tat org.junit.platform.engine.support.hierarchical.ForkJoinPoolHierarchicalTestExecutorService.joinConcurrentTasksInReverseOrderToEnableWorkStealing(ForkJoinPoolHierarchicalTestExecutorService.java:201)\n\tat org.junit.platform.engine.support.hierarchical.ForkJoinPoolHierarchicalTestExecutorService.invokeAll(ForkJoinPoolHierarchicalTestExecutorService.java:167)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.lambda$executeRecursively$6(NodeTestTask.java:160)\n\tat org.junit.platform.engine.support.hierarchical.ThrowableCollector.execute(ThrowableCollector.java:73)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.lambda$executeRecursively$8(NodeTestTask.java:146)\n\tat org.junit.platform.engine.support.hierarchical.Node.around(Node.java:137)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.lambda$executeRecursively$9(NodeTestTask.java:144)\n\tat org.junit.platform.engine.support.hierarchical.ThrowableCollector.execute(ThrowableCollector.java:73)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.executeRecursively(NodeTestTask.java:143)\n\tat org.junit.platform.engine.support.hierarchical.NodeTestTask.execute(NodeTestTask.java:100)\n\tat org.junit.platform.engine.support.hierarchical.ForkJoinPoolHierarchicalTestExecutorService$ExclusiveTask.exec(ForkJoinPoolHierarchicalTestExecutorService.java:274)\n\tat java.base/java.util.concurrent.ForkJoinTask.doExec(ForkJoinTask.java:387)\n\tat java.base/java.util.concurrent.ForkJoinPool$WorkQueue.topLevelExec(ForkJoinPool.java:1312)\n\tat java.base/java.util.concurrent.ForkJoinPool.scan(ForkJoinPool.java:1843)\n\tat java.base/java.util.concurrent.ForkJoinPool.runWorker(ForkJoinPool.java:1808)\n\tat java.base/java.util.concurrent.ForkJoinWorkerThread.run(ForkJoinWorkerThread.java:188)\n"
}2.5. Headers
2.5.1. Request header
| Name | Description |
|---|---|
|
Optional request header with a UUID for the request, if not present the server will generate a UUID. If the provided UUID is invalid server will respond with HTTP code 400 |
|
Authentication is performed via HTTP Basic Auth, and an API key is provided as the basic auth username value and the API secret as the password value, username and password is expected to be separated with a ':'. This header is required. |
2.5.2. Response header
Every response has the following header(s):
| Name | Description |
|---|---|
|
A UUID for the request. Id can be provided in the request header, if not provided it will be generated by the server |
2.6. Pagination
All Encap REST APIs that returns a collection of data supports pagination.
2.6.1. Request
Pagination requests has the following request parameters:
| Parameter | Description |
|---|---|
|
Id of the first session to include in response. Offset is optional, if not provided the result will start with the first session in the device history |
|
The number of objects on each page. Limit is optional, if not provided the defualt of 100 will be used. |
2.6.2. Response
Pagination response has the following structure:
| Field | Type | Description |
|---|---|---|
|
|
Holds the url to the previous set of items |
|
|
Holds the url to the next set of items |
|
|
Offset as passed in request |
|
|
The number of items on each page |
|
|
Items contains a list of the paginated objects for the request |
Example of pagination response:
HTTP/1.1 200 OK
X-Correlation-UUID: 8e7764bb-ccda-4071-b7d6-3ae2225a09c0
Content-Type: application/json
Content-Length: 1541
{
"previous" : "/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/sessions?limit=3&offset=cd4e1f77-5b69-41fb-baba-370025c1512b",
"next" : "/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/sessions?limit=3&offset=893bfacd-7bbf-4a9a-bd3b-657d0212102a",
"offset" : "05aaf805-0d34-45d9-957e-0d8743398ffd",
"limit" : 3,
"items" : [ {
"session_id" : "83f2efe7-e88f-491b-a711-ca037458d747",
"device_id" : "fc1b53a7-0d77-4623-a76b-79b15d18c9fe",
"ref" : "/enrollments/83f2efe7-e88f-491b-a711-ca037458d747",
"purpose" : "ACTIVATION",
"state" : "SUCCESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:57.327UTC",
"session_expires_on" : "2025-10-28T13:49:57.327UTC",
"offline" : false
}, {
"session_id" : "ba751492-9d1f-4451-8504-aaeafada45c5",
"device_id" : "fc1b53a7-0d77-4623-a76b-79b15d18c9fe",
"ref" : "/authentications/ba751492-9d1f-4451-8504-aaeafada45c5",
"purpose" : "AUTHENTICATION",
"state" : "IN_PROGRESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:57.327UTC",
"session_expires_on" : "2025-10-28T13:49:57.327UTC",
"offline" : false
}, {
"session_id" : "ef81afe4-4adc-4806-936a-b9e74d5bb4cc",
"device_id" : "fc1b53a7-0d77-4623-a76b-79b15d18c9fe",
"purpose" : "DELETE_RECOVERY",
"state" : "IN_PROGRESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:57.327UTC",
"session_expires_on" : "2025-10-28T13:49:57.327UTC",
"offline" : false
} ]
}3. Smart Device API
3.1. Common objects
3.1.1. The risk attributes object
| Field | Type | Description |
|---|---|---|
|
|
The name of the risk attribute |
|
|
The value of the risk attribute |
Risk attributes
Encap can collect a set of risk attributes for each operation, what attributes to collect is configured in the application configuration
| Risk attribute | Config attribute | Type | Description | Platform |
|---|---|---|---|---|
|
|
String |
A fingerprint of the operating system. This can be used for detecting whether the device is running a custom ROM or operating system |
Android |
|
|
String |
The operating system version. Examples: 4.1.2, 6.0.1 |
iOS, Android |
|
|
String |
The input method that was used to enter text in the application. Can be used to detect when a custom keyboard is used on the device. For more info on input methods please see: https://developer.android.com/guide/topics/text/creating-input-method |
Android |
|
|
Boolean |
Indicate whether the application running can be debugged using a source level debugger, either by manifest entry or in emulator |
Android |
|
|
Boolean |
Indicate whether debug is enabled on device, either by user setting (USB-debugging enabled) or when running in emulator (debugging enabled by default) |
Android |
|
|
Boolean |
Indicate whether a debugger is connected to the application |
Android |
|
|
Boolean |
Indicate whether the application is running in an emulator |
Android |
|
|
Boolean |
Indicate whether the device has been rooted/jail-broken. For iOS this value has to be passed to Encap using the |
iOS, Android |
|
|
Boolean |
Indicate whether the device has secure screen enabled or not |
iOS, Android |
|
|
String |
The host address the request originated from. It will contain the value of X-Forwarded-For (XFF) header from the request and can contain multiple IP addresses depending on proxy and load balancers. If XFF is not present we will use the remote address of the request. It can be either the IP of the client or the last proxy that sent the request, it is specified by the value of the Common Gateway Interface (CGI) variable REMOTE_ADDR. |
iOS, Android |
|
|
Base64 |
SHA-256 hash of the public key of certificate of the application signer. If there are more signers, each hash is comma separated. This can be used for detecting whether the application has been re-signed. |
Android |
|
|
String |
HTTP User agent from smart device application. |
iOS, Android |
|
|
Base64 |
SHA256 hash of the unique hardware device ID of the client device. |
iOS, Android |
|
|
String |
The manufacturer of the device. Examples: "Apple", "Samsung". |
iOS, Android |
|
|
String |
The device’s model. Examples: "iPad2,2", "Nexus S". |
iOS, Android |
|
|
String |
Indicates the OperatingSystemType of the device, either Android or iOS. |
iOS, Android |
|
|
Base64 |
SHA256 hash of the application name. The server can use this for detecting re-packaging. |
iOS, Android |
|
|
JSON |
An array containing the client network interfaces. This includes the type of the network and the IP address, and the list can contain multiple interfaces if the user’s device is connected to more than one at the time of the transaction. Example: [{"Type":"Cellular","IPAddress":"123.123.123.123"},{"Type":"Wifi","IPAddress":"124.124.124.124"}] |
iOS, Android |
|
|
String |
The status of the hardware protected key signature preformed by the Encap client SDK. |
iOS, Android |
|
|
String |
The result of the hardware protected key signature verification on the Encap server. |
iOS, Android |
|
|
Integer |
Provide battery level of the device. |
iOS, Android |
|
|
Boolean |
Indicate whether the device is being charged/connected to a charger. |
iOS, Android |
|
|
Object |
Location data from the device. The response is part of the location object, and is not included as values in the risk attribute object. |
iOS, Android |
|
|
String |
Indicates the time zone setting of the device. |
iOS, Android |
|
|
String |
Indicates the locale setting of the device. |
iOS, Android |
|
|
Boolean |
Indicates whether the developer mode is enabled on the device or not. |
Android |
|
|
Boolean |
Indicates whether screen overlay is detected on the device or not. |
Android |
|
|
JSON |
An Array containing the magnetic field strength measurements with timestamp from the device’s magnetometer sensor. Example: "[{\"x\":1.0,\"y\":2.0,\"z\":3.0,\"timestamp\":\"2025-08-22T10:28:25.548UTC\"},{\"x\":1.1,\"y\":2.1,\"z\":3.1, \"timestamp\":\"2025-08-22T10:28:25.548UTC\"}]" |
iOS, Android |
|
|
JSON |
An Array containing atmospheric pressure measurements with timestamp from the device’s barometer sensor Example: "[{\"value\":1.0,\"timestamp\":\"2025-08-22T10:28:25.548UTC\"},{\"value\":1.1,\"timestamp\":\"2025-08-22T10:28:25.548UTC\"}]" |
iOS, Android |
|
|
JSON |
An array containing gravity force measurements with timestamp from the device’s gravity sensor Example: "[{\"x\":0.7,\"y\":3.3,\"z\":0.9, \"timestamp\":\"2025-08-22T10:28:25.548UTC\"},{\"x\":0.8,\"y\":3.2,\"z\":0.8, \"timestamp\":\"2025-08-22T10:28:25.548UTC\"}]" |
iOS, Android |
|
|
Base64 |
Provides the name of the Wi-Fi network the device is connected to. Example: "V0lGSV81Rw==" |
iOS, Android |
|
|
String |
Provides the MAC address of the Wi-Fi access point to which the device is connected to. Example: "00:14:22:01:23:45" |
iOS, Android |
|
|
Boolean |
Indicates whether VPN is currently active on the device or not. |
iOS, Android |
|
|
Boolean |
Indicate whether proxy is currently active on the device or not. |
iOS, Android |
Hardware protected key server result
These are the possible values for the hw_key_server_result attribute.
| Status | Description | Validation strategy |
|---|---|---|
SIGNATURE_VERIFICATION_SUCCESS |
Verification of the hardware protected key signature was successful |
Operation is successful in both strategy modes. |
SIGNATURE_VERIFICATION_FAILED |
Verification of the hardware protected key signature failed. |
Operation will fail in SUPPORTED mode. |
NOT_ACTIVATED_WITH_HW_KEY |
Signature could not be verified because registration was not activated with hardware protected keys. Only applicable for authentication. |
Operation will not fail regardless of strategy mode. |
NOT_PROVIDED_BY_CLIENT |
The client is on an Encap version that does not support the hardware protected key feature. Only applicable for enrollment. |
Operation will not fail regardless of strategy mode. The device will be activated without hardware protected keys, and the device will be able to perform all operations but will not be able to use the hardware protected key feature. |
Hardware protected key client statuses
These are the possible values for the hw_key_client_status attribute.
| Status | Description | Operation |
|---|---|---|
OK_KEY_PROVIDED |
Activation of hardware protected keys was successful on the client. |
Enrollment |
OK_SIGNED_SUCCESS |
Authentication challenge was successfully signed with the hardware protected key on the client. |
Authentication |
INFO_NO_HARDWARE_SUPPORT |
The client device does not have Secure Enclave, or it is running in a simulator. Only for iOS |
Enrollment |
INFO_NO_OPERATING_SYSTEM_SUPPORT |
The client operating system does not support hardware backed keys. It is supported on:
|
Enrollment |
INFO_NOT_ACTIVATED_WITH_HW_KEY |
The registration was not activated with hardware protected keys support for one or more of the following reasons:
|
Authentication |
ERR_KEY_GENERATION_FAILED |
Unexpected error during generation of keypair on client. |
Enrollment |
ERR_RETRIEVE_PUBLIC_KEY_FAILED |
Unexpected error retrieving public key. Only on iOS. |
Enrollment |
ERR_RETRIEVE_PRIVATE_KEY_REF_FAILED |
Unexpected error when retrieving reference to private key. |
Enrollment and Authentication |
ERR_SIGN_OPERATION_FAILED |
Unexpected error when generating signature. |
Enrollment and Authentication |
3.1.2. The location object
Encap can collect the location of the device for each operation, given that it is enabled in the application configuration. This requires the end user to give the application permission to use the location of the device.
| Field | Type | Description |
|---|---|---|
|
|
Location accuracy |
|
|
Location altitude |
|
|
Location latitude |
|
|
Location longitude |
3.1.3. The operation context object
| Field | Type | Description |
|---|---|---|
|
|
Context title, that is base64 encoded twice. The double base64 encoding is a bug, the documentation will be updated once it’s fixed |
|
|
Context content, that is base64 encoded twice. The double base64 encoding is a bug, the documentation will be updated once it’s fixed |
|
|
The MIME type of the content |
3.1.4. The session status object
| Field | Type | Description |
|---|---|---|
|
|
The status of the session. See session status for details. |
|
|
A description of the session status |
|
|
The state of the session. See session state for details. |
Session statuses
| Session Status | Description |
|---|---|
|
Operation is in progress |
|
Operation is authenticated, but not complete |
|
Operation has completed successfully |
|
Operation failed because the session was cancelled by the device |
|
Operation failed because the session was cancelled by the service provider |
|
Operation failed because the session was cancelled by the device. The device started a deactivation of authentication method(s) |
|
Operation failed because the session was cancelled when a reactivation was started |
|
Operation failed because the session has expired |
|
Operation failed because the device is locked |
|
Operation failed because the device is locked by admin |
|
Operation failed because the device is locked by device verification |
|
Operation failed because the device is locked due to a second factor verification failure (incorrect PIN code or biometrics) |
|
Operation failed because the device is locked by incorrect salt key id |
|
Operation failed because the session callback failed. Legacy value from synchronous callback model. |
|
Operation failed because the device provided incorrect signed challenge |
|
Operation failed because the SafetyNet attestation validation failed |
|
Operation failed because the intermediate push attestation validation failed |
|
Operation failed because of missing intermediate push attestation details |
|
Operation failed because of missing SafetyNet attestation details |
|
Operation failed because authorization token validation failed |
|
Operation failed because the session was cancelled when recovery was started |
|
Operation failed because the recovery does not exist |
|
Operation failed because the recovery is locked |
|
Operation failed because the geofencing validation failed |
|
Operation failed because the App Attest validation failed |
|
Operation failed because of missing App Attest attestation details |
|
Operation failed because the Play Integrity validation failed |
|
Operation failed because of missing Play Integrity attestation details |
|
Operation failed unexpectedly |
|
Operation failed because Server Side Face adapter encountered an error |
|
Operation failed because Server Side Face verification failed |
|
Operation failed because a replay attempt was blocked by the Server Side Face adapter |
Session states
| Session State | Description |
|---|---|
|
Session is in progress |
|
Session has completed successfully |
|
Operation and session failed |
3.1.5. The attestation object
| Field | Type | Description |
|---|---|---|
|
|
Play Integrity attestation status for the device |
|
|
Date of when the Play Integrity attestation was performed |
|
|
SafetyNet attestation status for the device |
|
|
Date of when the SafetyNet attestation was performed |
|
|
App Attest attestation status for the device. Only for iOS devices |
|
|
Date of when the App Attest attestation was performed. Only for iOS devices |
App Attest statuses
| App Attest status | Description |
|---|---|
|
Attestation verification was successful |
|
Attestation failed because the Apple App Attest server was unavailable |
|
Attestation failed because App Attest is not supported on device |
|
Attestation failed because of an unexpected error; check the error message for details |
|
Attestation failed because the request took longer than the configured timeout |
|
Validation of the attestation object failed because the integrity check failed |
Play Integrity statuses
| Google Play Integrity status | Description |
|---|---|
|
Attestation verification was successful |
|
Attestation failed because the integrity check failed |
|
Attestation failed because the Google Play app is unrecognized |
|
Attestation failed because the Google Play app is unlicensed |
|
Attestation failed because of incorrect package name |
|
Attestation failed because of invalid JWS format |
|
Attestation failed because Google Play Integrity returned an API exception |
|
Attestation failed due to request taking longer than the configured timeout |
|
Attestation failed because of incorrect nonce |
|
Attestation failed because of missing JWS |
|
Attestation failed because of missing status returned from the client |
|
Attestation failed because the timestamp is not within the lifetime of the Encap server session |
|
Attestation failed due to client doesn’t have Google Play or the version is too old |
SafetyNet statuses
| SafetyNet status | Description |
|---|---|
|
Attestation verification was successful |
|
Attestation failed because the signature is invalid |
|
Attestation failed because the integrity check failed |
|
Attestation failed because of incorrect package name |
|
Attestation failed because of incorrect certificate digest |
|
Attestation failed because of invalid hostname |
|
Attestation failed because of invalid JWS format |
|
Attestation failed because SafetyNet returned an API exception |
|
Attestation failed due to request taking longer than the configured timeout |
|
Attestation failed due to missing API key |
|
Attestation failed because of incorrect nonce |
|
Attestation failed because of missing JWS |
|
Attestation failed because of missing status returned from the client |
|
Attestation failed because the timestamp is not within the lifetime of the session |
|
Attestation failed due to client doesn’t have Google Play or the version is too old |
3.1.6. The geofencing object
| Field | Type | Description |
|---|---|---|
|
|
Country code on ISO 3166-1 Alpha-2 format. |
|
|
Status of the geofencing client operation. |
|
|
Status of the geofencing server validation. |
Geofencing client statuses
| Geofencing Client Status | Description |
|---|---|
|
Country code obtained. |
|
Location not requested by app or user declined. |
|
Device did not obtain a location within configured accuracy before timeout. |
|
Location was mocked/faked. |
|
Geocoder not supported on device. |
|
Geocoder network or service not available. |
|
Unexpected geocoder error. |
|
Geocoder call did not finish within time limit. |
|
The reverse geocode request yielded an empty result for current location. |
3.1.7. The recovery object
| Field | Type | Description |
|---|---|---|
|
|
Identifier of a given recovery. |
|
|
The recovery method used to set up the recovery. |
|
|
The recovery status of a given recovery. |
|
|
Date for when a given recovery was has been created. |
|
|
Date for when a given recovery has been updated. |
|
|
Date for when a given recovery has been used. |
Recovery status
| Recovery status | Description |
|---|---|
|
Recovery has been set up for the device and is ready to be used. |
|
Recovery has been deactivated. |
|
Recovery has been used to recover the device. |
|
Recovery has been locked. |
Recovery method
| Recovery method | Description |
|---|---|
|
Recovery is based on cloud backup, and a recovery key locked with PIN |
|
Recovery is based on cloud backup, and a recovery key locked with Server Side Face authentication |
3.2. Constants
3.2.1. Authentication methods
| Authentication method (Variant 1) | Authentication method (Variant 2) | Description |
|---|---|---|
|
|
Device |
|
|
PIN |
|
|
FaceID for iOS |
|
|
Fingerprint for Android |
|
|
TouchID for iOS where the registered fingerprints at activation time cannot be updated |
|
|
Biometric prompt for Android |
|
|
Server Side Face authentication |
|
|
Device (offline authentication) |
|
|
PIN (offline authentication) |
|
|
TouchID for iOS (offline authentication) |
|
|
Biometric prompt for Android (offline authentication) |
|
|
Fingerprint for Android (offline authentication) |
|
|
FaceID for iOS (offline authentication) |
3.2.2. Authentication levels
| Authentication level | Description |
|---|---|
|
Authentication level for one factor |
|
Authentication level for two factors |
3.2.3. Lock reason
| Lock reason | Description |
|---|---|
|
Device is unlocked |
|
The verification of one of the authentication factors failed. Wrong device and/or a second-factor error (incorrect PIN code or biometrics) |
|
The device is locked by an administrative operation |
|
The verification of the device factor failed for an authentication |
|
The verification of the second authentication factor failed (incorrect PIN code or biometrics) |
|
The device provided an incorrect Salt-key ID during authentication |
|
The verification of the hardware-protected key failed (the key provided was incorrect) |
|
The device is locked due to a failed offline authentication, caused by OTP verification code mismatch |
|
The verification of the SafetyNet attestation failed |
|
The verification of the intermediate push attestation failed |
|
The verification of the App Attest attestation failed |
|
The verification of the Play Integrity attestation failed |
3.2.4. Session purpose
| Purpose | Description |
|---|---|
|
Activation/enrollment of new device. |
|
Authentication. |
|
Activating an additional auth method for an existing device. |
|
Deactivating an auth method for an existing device. |
|
Setting up recovery for an existing device. |
|
An existing recovery has been used to perform a recovery to a new device. |
|
An existing recovery has been deleted. |
|
A notification sent to the old device when performing a recovery. |
3.3. Enrollment
Enrollments are used to create a binding between a supported customer mobile device/application instance and the Encap server, which can then be used for subsequent secure mobile authentication operations.
When enrollment is started, the Encap server returns a unique activation code which must be conveyed to the customer and supplied to the mobile application instance along with any additional biometric or non-biometric authentication factors. The underlying Encap mobile authentication technology will then complete a complex cryptographic handshake between the application instance and the Encap server which results in a secure binding between the application instance and the service, completing the enrollment process.
It is the responsibility of the client to establish a suitably secure trust channel in order to convey the activation code to the customer. For example, this can be done by displaying the code QR format in a previously-authenticated web session, where it can be captured by the device camera, but ultimately any secure, trusted channel can be used.
The enrollment process is asynchronous – a start operation is used to commence enrollment which then proceeds in the background. Successful completion or failure of an ongoing enrollment process can then be detected either by polling additional API operations or via a client-supplied REST callback interface. These two styles are illustrated below:
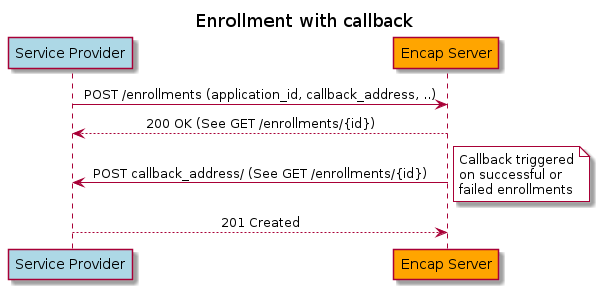
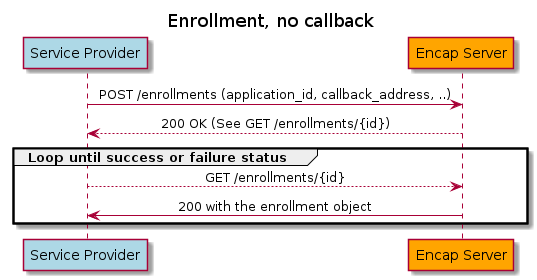
3.3.1. The enrollment object
| Field | Type | Description |
|---|---|---|
|
|
The UUID for the enrollment session |
|
|
The code to use for activation |
|
|
The application ID for the device |
|
|
The callback address for the device |
|
|
The UUID for the device |
|
|
The time for when the session was created. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The time for when the session will expire. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The authentication level of the enrollment. See authentication levels for options |
|
|
List of activated authentication methods (Variant 2). See authentication methods for possible values |
|
|
The push address for the device, this address is used when sending push to the device using FCM or APNS. |
|
|
A custom payload send to the device in the push notification. |
|
|
Explicit setting for the device to lock/unlock recovery. |
|
|
Operation context object that contains details to be shown after a successful the authentication. See operation_context object for details. |
|
|
Attestation object that contains details for all the attestations performed for the device. See attestation object for details. |
|
|
List that contains name and value for all risk attributes. See risk_attributes object for details. |
|
|
Status object that contains status details of the session. See session_status object for details. |
|
|
Location object that contains location details, see location object for details. |
|
|
Geofencing object that contains details of device location and geofencing validation. See geofencing object for details. |
3.3.2. Start enrollment of device
POST /api/smart-device/v1/enrollments
To start an enrollment of a device you create an enrollment object
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
The application id for the configuration to use during the enrollment |
|
|
No |
The authentication level for the operation. See authentication levels for options. If not provided default level TWO_FACTOR will be used |
|
|
No |
The callback address for the device |
|
|
No |
Life time in ms for for the session before it expires |
|
|
No |
A custom payload send to the device in the push notification, the payload can maximum contain 256 bytes and all characters must be in the Basic Multilingual Plane. Please note that the payload is sent in plain text and that the push channel is not a secure channel, to send data to the device over a secure channel use the post/pre operation context. |
|
|
No |
Allows to override recovery setting from app config and disable recovery during REST enrollment. |
|
|
No |
Operation context object that contains details to be shown after a successful the authentication. See operation_context object for details. |
Example request body
{
"application_id" : "encap",
"session_expiry_time" : 3000,
"callback_address" : "http://callback.url.com",
"post_operation_context" : {
"context_title_b64" : "VG1salpWUnBkR3hs",
"context_content_b64" : "VG1salpWUnBkR3hs",
"context_mime" : "text/plain"
},
"authentication_level" : "ONE_FACTOR",
"custom_push_payload" : "ServerA",
"recovery_lock" : false
}Returns
Returns an enrollment object if the enrollment process is successfully initiated. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/enrollments' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"application_id" : "encap",
"session_expiry_time" : 3000,
"callback_address" : "http://callback.url.com",
"post_operation_context" : {
"context_title_b64" : "VG1salpWUnBkR3hs",
"context_content_b64" : "VG1salpWUnBkR3hs",
"context_mime" : "text/plain"
},
"authentication_level" : "ONE_FACTOR",
"custom_push_payload" : "ServerA",
"recovery_lock" : false
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: 31b0cbae-d037-4fb4-9305-6f8fda55bffb
Content-Type: application/json
Content-Length: 1809
{
"id" : "aa8bada0-a52a-4cad-a2db-8f2b81679abb",
"application_id" : "encap",
"activation_code" : "123456",
"callback_address" : "callback",
"device_id" : "4da67877-04ce-41c4-a588-a009432997f5",
"session_created_time" : "2025-10-28T13:49:59.111UTC",
"session_expiry_time" : "2025-10-28T15:49:59.111UTC",
"authentication_level" : "TWO_FACTOR",
"activated_authentication_methods" : [ "DEVICE", "DEVICE:PIN" ],
"location" : {
"accuracy" : "0.564",
"altitude" : "76.2352.3563",
"latitude" : "12.34234.143",
"longitude" : "32.24314.1431"
},
"post_operation_context" : {
"context_title_b64" : "VkdsMGJHVT0=",
"context_content_b64" : "UTI5dWRHVnVkQT09",
"context_mime" : "MIME"
},
"risk_attributes" : [ {
"name" : "is_debuggable",
"value" : "true"
}, {
"name" : "is_debugger_connected",
"value" : "true"
}, {
"name" : "input_method",
"value" : "input"
}, {
"name" : "is_emulator",
"value" : "true"
}, {
"name" : "operating_system_version",
"value" : "2.3"
}, {
"name" : "client_side_ip",
"value" : "[\"192.168.0.1\"]"
} ],
"session_status" : {
"status" : "IN_PROGRESS",
"description" : "Operation is in progress",
"state" : "IN_PROGRESS"
},
"attestation" : {
"safety_net_status" : "VERIFIED",
"safety_net_date" : "2025-10-28T13:49:59.111UTC",
"app_attest_status" : "VERIFIED",
"app_attest_date" : "2025-10-28T13:49:59.111UTC",
"play_integrity_status" : "VERIFIED",
"play_integrity_date" : "2025-10-28T13:49:59.111UTC"
},
"geofencing" : {
"country_code" : "NO",
"client_status" : "OK",
"server_boundary_validation" : "SUCCESS"
},
"push_address" : "123409238402394f3413r2e2f",
"custom_push_payload" : "ServerA",
"recovery_lock" : false
}3.3.3. Get enrollment details
GET /api/smart-device/v1/enrollments/{id}
Getting the enrollment details lets you know the state of the enrollment and if finished it gives you access to risk data and all other attributes created as part of the enrollment process.
Returns
Returns an enrollment object if a valid identifier was provided, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/enrollments/aa8bada0-a52a-4cad-a2db-8f2b81679abb' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 3eb19529-5bef-49d3-9bf6-c3a397819749
Content-Type: application/json
Content-Length: 1809
{
"id" : "aa8bada0-a52a-4cad-a2db-8f2b81679abb",
"application_id" : "encap",
"activation_code" : "123456",
"callback_address" : "callback",
"device_id" : "7769483a-15bb-47de-b380-82a93c88808a",
"session_created_time" : "2025-10-28T13:49:59.324UTC",
"session_expiry_time" : "2025-10-28T15:49:59.324UTC",
"authentication_level" : "TWO_FACTOR",
"activated_authentication_methods" : [ "DEVICE", "DEVICE:PIN" ],
"location" : {
"accuracy" : "0.564",
"altitude" : "76.2352.3563",
"latitude" : "12.34234.143",
"longitude" : "32.24314.1431"
},
"post_operation_context" : {
"context_title_b64" : "VkdsMGJHVT0=",
"context_content_b64" : "UTI5dWRHVnVkQT09",
"context_mime" : "MIME"
},
"risk_attributes" : [ {
"name" : "is_debuggable",
"value" : "true"
}, {
"name" : "is_debugger_connected",
"value" : "true"
}, {
"name" : "input_method",
"value" : "input"
}, {
"name" : "is_emulator",
"value" : "true"
}, {
"name" : "operating_system_version",
"value" : "2.3"
}, {
"name" : "client_side_ip",
"value" : "[\"192.168.0.1\"]"
} ],
"session_status" : {
"status" : "IN_PROGRESS",
"description" : "Operation is in progress",
"state" : "IN_PROGRESS"
},
"attestation" : {
"safety_net_status" : "VERIFIED",
"safety_net_date" : "2025-10-28T13:49:59.324UTC",
"app_attest_status" : "VERIFIED",
"app_attest_date" : "2025-10-28T13:49:59.324UTC",
"play_integrity_status" : "VERIFIED",
"play_integrity_date" : "2025-10-28T13:49:59.324UTC"
},
"geofencing" : {
"country_code" : "NO",
"client_status" : "OK",
"server_boundary_validation" : "SUCCESS"
},
"push_address" : "123409238402394f3413r2e2f",
"custom_push_payload" : "ServerA",
"recovery_lock" : false
}3.3.4. Cancel enrollment
DELETE /api/smart-device/v1/enrollments/{sessionId}
To cancel an enrollment in progress thereby preventing the device from finishing the enrollment process
Returns
Returns 204 No Content if a valid identifier was provided and the process was canceled. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/enrollments/aa8bada0-a52a-4cad-a2db-8f2b81679abb' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: b6361b11-27c8-43e4-9300-2deb3413a48d3.3.5. Callback
If ´callback_address´ is set, this will be a POST to the Service Provider’s ´callback_address´ with an enrollment object identical to the object that the Service Provider would get if get enrollment details was called.
See callback implementation and callback usage for more details.
Example request
POST /api/callback/v1/enroll HTTP/1.1
Content-Type: application/json
Content-Length: 1321
Host: localhost:8080
{
"id" : "b93046fc-8502-4355-a253-5a994e2772ed",
"application_id" : "encap",
"activation_code" : "123456",
"callback_address" : "http://callback.url.com",
"device_id" : "8e57f444-641f-42d3-a46a-6f393137382e",
"session_created_time" : "2025-10-28T13:49:58.964UTC",
"session_expiry_time" : "2025-10-28T13:49:58.964UTC",
"authentication_level" : "TWO_FACTOR",
"activated_authentication_methods" : [ "DEVICE", "DEVICE:PIN" ],
"location" : {
"accuracy" : "0.564",
"altitude" : "76.2352.3563",
"latitude" : "12.34234.143",
"longitude" : "32.24314.1431"
},
"post_operation_context" : {
"context_title_b64" : "VG1salpWUnBkR3hs",
"context_content_b64" : "VG1salpWUnBkR3hs",
"context_mime" : "text/plain"
},
"risk_attributes" : [ {
"name" : "is_debuggable",
"value" : "true"
}, {
"name" : "is_debugger_connected",
"value" : "true"
}, {
"name" : "input_method",
"value" : "input"
}, {
"name" : "is_emulator",
"value" : "true"
}, {
"name" : "operating_system_version",
"value" : "2.3"
}, {
"name" : "client_side_ip",
"value" : "[\"192.168.0.1\"]"
} ],
"session_status" : {
"status" : "SUCCESS",
"description" : "Operation has completed successfully",
"state" : "SUCCESS"
},
"recovery_lock" : false
}Example response
HTTP/1.1 200 OK3.3.6. Re-enrollment
Re-enrollment enables users to be re-enrolled and create new credentials on the same device ID given that they are still using the same device as they were originally enrolled on. This will remove complexity from Service Providers allowing them to reuse the device ID instead of creating a new one.
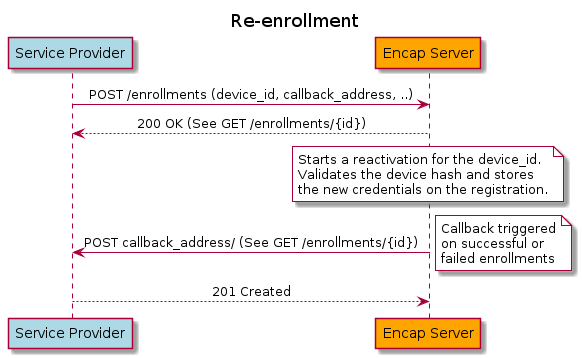
Limitations
-
Re-enrollment does not work on registrations that has been deactivated either by the Service Provider or by the end-user. In these scenarios the user needs to start a new enrollment.
-
End-user must be on the same device. Encap validates the device hash during the re-enrollment to confirm that the end-user is still using the same device. Generally, the device hash will remain unchanged after a re-installation of the app, but we have identified the following exceptions:
-
Android:
-
Factory reset may change the device hash.
-
Reinstalling the app after an upgrade from Android version 7 or below to 8 or above will cause changes to the device hash.
-
The device hash will not be carried over to a new device.
-
-
iOS:
-
Reinstalling the app from a non-encrypted backup after a factory reset
-
The device hash will not be carried over to a new device.
-
-
Start re-enrollment of device
POST /api/smart-device/v1/enrollments
To start a re-enrollment of a device you create an enrollment object that contains device_id parameter.
application_id is optional in this case.
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
The device id for the configuration to use during the re-enrollment |
|
|
No |
The application id for the configuration to use during the enrollment. If not provided we will use application id of the old registration.It is not allowed to change application id in e re-enrollment, if application id is provided it has to match the application id of the old registration. |
|
|
No |
The authentication level for the operation. See authentication levels for options. If not provided default level TWO_FACTOR will be used |
|
|
No |
The callback address for the device |
|
|
No |
Life time in ms for for the session before it expires |
|
|
No |
A custom payload send to the device in the push notification, the payload can maximum contain 256 bytes and all characters must be in the Basic Multilingual Plane. Please note that the payload is sent in plain text and that the push channel is not a secure channel, to send data to the device over a secure channel use the post/pre operation context. |
|
|
No |
Operation context object that contains details to be shown after a successful the authentication. See operation_context object for details. |
Example request body
{
"application_id" : "encap",
"session_expiry_time" : 3000,
"callback_address" : "http://callback.url.com",
"post_operation_context" : {
"context_title_b64" : "VG1salpWUnBkR3hs",
"context_content_b64" : "VG1salpWUnBkR3hs",
"context_mime" : "text/plain"
},
"authentication_level" : "ONE_FACTOR",
"custom_push_payload" : "ServerA",
"device_id" : "c473c2ce-3c89-4568-83bc-24eb0f458d41"
}Returns
Returns an enrollment object if the enrollment process is successfully initiated. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/enrollments' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"application_id" : "encap",
"session_expiry_time" : 3000,
"callback_address" : "http://callback.url.com",
"post_operation_context" : {
"context_title_b64" : "VG1salpWUnBkR3hs",
"context_content_b64" : "VG1salpWUnBkR3hs",
"context_mime" : "text/plain"
},
"authentication_level" : "ONE_FACTOR",
"custom_push_payload" : "ServerA",
"device_id" : "c473c2ce-3c89-4568-83bc-24eb0f458d41"
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: 95f59d41-bdca-43d5-9b79-8267ec9ad3ea
Content-Type: application/json
Content-Length: 1809
{
"id" : "aa8bada0-a52a-4cad-a2db-8f2b81679abb",
"application_id" : "encap",
"activation_code" : "123456",
"callback_address" : "callback",
"device_id" : "5e1d7f88-8833-4d11-b158-6fa329d480db",
"session_created_time" : "2025-10-28T13:49:59.378UTC",
"session_expiry_time" : "2025-10-28T15:49:59.378UTC",
"authentication_level" : "TWO_FACTOR",
"activated_authentication_methods" : [ "DEVICE", "DEVICE:PIN" ],
"location" : {
"accuracy" : "0.564",
"altitude" : "76.2352.3563",
"latitude" : "12.34234.143",
"longitude" : "32.24314.1431"
},
"post_operation_context" : {
"context_title_b64" : "VkdsMGJHVT0=",
"context_content_b64" : "UTI5dWRHVnVkQT09",
"context_mime" : "MIME"
},
"risk_attributes" : [ {
"name" : "is_debuggable",
"value" : "true"
}, {
"name" : "is_debugger_connected",
"value" : "true"
}, {
"name" : "input_method",
"value" : "input"
}, {
"name" : "is_emulator",
"value" : "true"
}, {
"name" : "operating_system_version",
"value" : "2.3"
}, {
"name" : "client_side_ip",
"value" : "[\"192.168.0.1\"]"
} ],
"session_status" : {
"status" : "IN_PROGRESS",
"description" : "Operation is in progress",
"state" : "IN_PROGRESS"
},
"attestation" : {
"safety_net_status" : "VERIFIED",
"safety_net_date" : "2025-10-28T13:49:59.378UTC",
"app_attest_status" : "VERIFIED",
"app_attest_date" : "2025-10-28T13:49:59.378UTC",
"play_integrity_status" : "VERIFIED",
"play_integrity_date" : "2025-10-28T13:49:59.378UTC"
},
"geofencing" : {
"country_code" : "NO",
"client_status" : "OK",
"server_boundary_validation" : "SUCCESS"
},
"push_address" : "123409238402394f3413r2e2f",
"custom_push_payload" : "ServerA",
"recovery_lock" : false
}3.4. Authentication
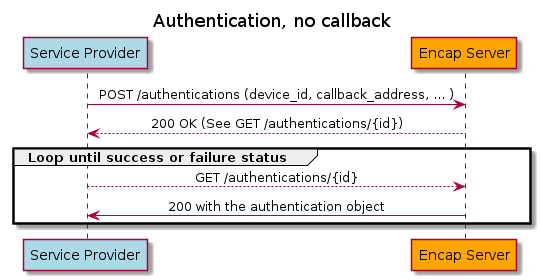
Authentication operations are used to authenticate customers via previously-enrolled device/application instances. The authentication process is fully contextual, with context information supplied via the API that can be displayed to the customer before and/or after authentication has completed.
The authentication process is asynchronous – a start operation is used to commence an authentication process which then proceeds in the background. Successful completion or failure of an ongoing authentication process can then be detected either by polling via additional API requests or via a client-implemented REST callback interface. These two styles are illustrated below:
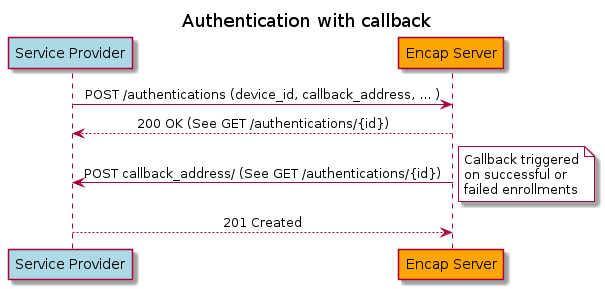
3.4.1. The authentication object
| Field | Type | Description |
|---|---|---|
|
|
The UUID for the authentication session |
|
|
The authentication level of the enrollment. See authentication levels for options |
|
|
The authentication method for the operation (Variant 1). See authentication methods for possible values |
|
|
The callback address for the device |
|
|
The UUID for the device |
|
|
Boolean for if a push has been sent or not |
|
|
The time for when the session was created. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The time for when the session will expire. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The purpose of the session. See session purpose for details. |
|
|
A string (UTF-8 3-byte characters) passed as client data from the client SDK in start authentication. |
|
|
A custom payload send to the device in the push notification. |
|
|
Operation context object that contains details to be shown before the authentication.See operation_context object for details. |
|
|
Operation context object that contains details to be shown after a successful the authentication. See operation_context object for details. |
|
|
List that contains name and value for all risk attributes. See risk_attributes object for details. |
|
|
Location object that contains location details, see location object for details. |
|
|
Status object that contains status details of the session. See session_status object for details. |
|
|
Attestation object that contains details for all the attestations performed for the device. See attestation object for details. |
|
|
Geofencing object that contains details of device location and geofencing validation. See geofencing object for details. |
3.4.2. Start authentication
POST /api/smart-device/v1/authentications
To start an authentication you create an authentication object
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
The UUID for the device |
|
|
No |
The authentication level for the operation. See authentication levels for options. If not provided default level TWO_FACTOR will be used |
|
|
No |
The authentication method for the operation (Variant 1). See authentication methods for possible values |
|
|
No |
The callback address for the device |
|
|
No |
Life time in ms for for the session before it expires |
|
|
No |
A custom payload send to the device in the push notification, the payload can maximum contain 256 bytes and all characters must be in the Basic Multilingual Plane. Please note that the payload is sent in plain text and that the push channel is not a secure channel, to send data to the device over a secure channel use the post/pre operation context. |
|
|
No |
Choose to send push or not. It requires that push notifications are allowed for the given appId. Default is true. |
|
|
No |
Operation context object that contains details to be shown before the authentication.See operation_context object for details. |
|
|
No |
Operation context object that contains details to be shown after a successful the authentication. See operation_context object for details. |
Example request body
{
"device_id" : "a4984a53-0f60-48ea-afc8-e7858777611b",
"authentication_level" : "TWO_FACTOR",
"authentication_method" : "DEVICE_PIN",
"callback_address" : "http://callback.url.com",
"session_expiry_time" : 30000,
"pre_operation_context" : {
"context_title_b64" : "VUhKbFZHbDBiR1U9",
"context_content_b64" : "VUhKbFEyOXVkR1Z1ZEE9PQ==",
"context_mime" : "text/plain"
},
"post_operation_context" : {
"context_title_b64" : "VUc5emRGUnBkR3hs",
"context_content_b64" : "VUc5emRFTnZiblJsYm5RPQ==",
"context_mime" : "text/plain"
},
"send_push" : true,
"custom_push_payload" : "ServerA"
}Returns
Returns an authentication object if authentication process is successfully initiated. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/authentications' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"device_id" : "a4984a53-0f60-48ea-afc8-e7858777611b",
"authentication_level" : "TWO_FACTOR",
"authentication_method" : "DEVICE_PIN",
"callback_address" : "http://callback.url.com",
"session_expiry_time" : 30000,
"pre_operation_context" : {
"context_title_b64" : "VUhKbFZHbDBiR1U9",
"context_content_b64" : "VUhKbFEyOXVkR1Z1ZEE9PQ==",
"context_mime" : "text/plain"
},
"post_operation_context" : {
"context_title_b64" : "VUc5emRGUnBkR3hs",
"context_content_b64" : "VUc5emRFTnZiblJsYm5RPQ==",
"context_mime" : "text/plain"
},
"send_push" : true,
"custom_push_payload" : "ServerA"
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: f046f8f3-51d2-4a5e-8962-a9183c833ebe
Content-Type: application/json
Content-Length: 1916
{
"id" : "8865f08b-48a2-4c74-8124-b5f8d0fd68b1",
"authentication_level" : "TWO_FACTOR",
"authentication_method" : "DEVICE_PIN",
"callback_address" : "callback",
"device_id" : "980fe26f-9d7b-4cf2-8ddf-1804e9a2768e",
"push_sent" : true,
"custom_push_payload" : "ServerA",
"session_created_time" : "2025-10-28T13:49:57.919UTC",
"session_expiry_time" : "2025-10-28T15:49:57.919UTC",
"pre_operation_context" : {
"context_title_b64" : "VUhKbFZHbDBiR1U9",
"context_content_b64" : "VUhKbFEyOXVkR1Z1ZEE9PQ==",
"context_mime" : "MIME"
},
"post_operation_context" : {
"context_title_b64" : "VUc5emRGUnBkR3hs",
"context_content_b64" : "VUc5emRFTnZiblJsYm5RPQ==",
"context_mime" : "MIME"
},
"location" : {
"accuracy" : "0.564",
"altitude" : "76.2352.3563",
"latitude" : "12.34234.143",
"longitude" : "32.24314.1431"
},
"session_status" : {
"status" : "IN_PROGRESS",
"description" : "Operation is in progress",
"state" : "IN_PROGRESS"
},
"risk_attributes" : [ {
"name" : "is_debuggable",
"value" : "true"
}, {
"name" : "is_debugger_connected",
"value" : "true"
}, {
"name" : "input_method",
"value" : "input"
}, {
"name" : "is_emulator",
"value" : "true"
}, {
"name" : "operating_system_version",
"value" : "2.3"
}, {
"name" : "client_side_ip",
"value" : "[\"192.168.0.1\"]"
} ],
"client_data" : "YWJjZGVmMTIzNDU2",
"attestation" : {
"safety_net_status" : "VERIFIED",
"safety_net_date" : "2025-10-28T13:49:57.916UTC",
"app_attest_status" : "VERIFIED",
"app_attest_date" : "2025-10-28T13:49:57.916UTC",
"play_integrity_status" : "VERIFIED",
"play_integrity_date" : "2025-10-28T13:49:57.916UTC"
},
"geofencing" : {
"country_code" : "NO",
"client_status" : "OK",
"server_boundary_validation" : "SUCCESS"
},
"purpose" : "AUTHENTICATION"
}3.4.3. Get authentication details
GET /api/smart-device/v1/authentications/{id}
Getting the authentication details lets you know the state of the authentication and if finished it gives you access to risk data and all other attributes created as part of the authentication process.
Returns
Returns an authentication object if a valid identifier was provided, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/authentications/8865f08b-48a2-4c74-8124-b5f8d0fd68b1' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 0b2d7cc2-4910-4251-8624-bc531e3ca04c
Content-Type: application/json
Content-Length: 1916
{
"id" : "8865f08b-48a2-4c74-8124-b5f8d0fd68b1",
"authentication_level" : "TWO_FACTOR",
"authentication_method" : "DEVICE_PIN",
"callback_address" : "callback",
"device_id" : "abd77e5f-401b-4b16-94ac-ff93c817cec6",
"push_sent" : true,
"custom_push_payload" : "ServerA",
"session_created_time" : "2025-10-28T13:49:58.381UTC",
"session_expiry_time" : "2025-10-28T15:49:58.381UTC",
"pre_operation_context" : {
"context_title_b64" : "VUhKbFZHbDBiR1U9",
"context_content_b64" : "VUhKbFEyOXVkR1Z1ZEE9PQ==",
"context_mime" : "MIME"
},
"post_operation_context" : {
"context_title_b64" : "VUc5emRGUnBkR3hs",
"context_content_b64" : "VUc5emRFTnZiblJsYm5RPQ==",
"context_mime" : "MIME"
},
"location" : {
"accuracy" : "0.564",
"altitude" : "76.2352.3563",
"latitude" : "12.34234.143",
"longitude" : "32.24314.1431"
},
"session_status" : {
"status" : "IN_PROGRESS",
"description" : "Operation is in progress",
"state" : "IN_PROGRESS"
},
"risk_attributes" : [ {
"name" : "is_debuggable",
"value" : "true"
}, {
"name" : "is_debugger_connected",
"value" : "true"
}, {
"name" : "input_method",
"value" : "input"
}, {
"name" : "is_emulator",
"value" : "true"
}, {
"name" : "operating_system_version",
"value" : "2.3"
}, {
"name" : "client_side_ip",
"value" : "[\"192.168.0.1\"]"
} ],
"client_data" : "YWJjZGVmMTIzNDU2",
"attestation" : {
"safety_net_status" : "VERIFIED",
"safety_net_date" : "2025-10-28T13:49:58.372UTC",
"app_attest_status" : "VERIFIED",
"app_attest_date" : "2025-10-28T13:49:58.372UTC",
"play_integrity_status" : "VERIFIED",
"play_integrity_date" : "2025-10-28T13:49:58.372UTC"
},
"geofencing" : {
"country_code" : "NO",
"client_status" : "OK",
"server_boundary_validation" : "SUCCESS"
},
"purpose" : "AUTHENTICATION"
}3.4.4. Cancel authentication
DELETE /api/smart-device/v1/authentications/{sessionId}
To cancel an authentication in progress thereby preventing the device from finishing the authentication process
Returns
Returns 204 No Content if a valid identifier was provided and the process was canceled. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/authentications/8865f08b-48a2-4c74-8124-b5f8d0fd68b1' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: ff894b15-b4c1-4b32-9cf4-b573f192befc3.4.5. Callback
If ´callback_address´ is set, this will be a POST to the Service Provider’s ´callback_address´ with an authentication object identical to the object that the Service Provider would get if get authentication details was called.
See callback implementation and callback usage for more details.
Example request
POST /api/callback/v1/auth HTTP/1.1
Content-Type: application/json
Content-Length: 1409
Host: localhost:8080
{
"id" : "701c5227-99a5-4ef7-9575-f8cae9b49984",
"authentication_level" : "TWO_FACTOR",
"authentication_method" : "DEVICE_PIN",
"callback_address" : "http://callback.url.com",
"device_id" : "fd233996-1b66-443e-a4da-aad3086b3667",
"push_sent" : false,
"session_created_time" : "2025-10-28T13:49:55.933UTC",
"session_expiry_time" : "2025-10-28T13:49:55.933UTC",
"pre_operation_context" : {
"context_title_b64" : "VUhKbFZHbDBiR1U9",
"context_content_b64" : "VUhKbFEyOXVkR1Z1ZEE9PQ==",
"context_mime" : "text/plain"
},
"post_operation_context" : {
"context_title_b64" : "VUc5emRGUnBkR3hs",
"context_content_b64" : "VUc5emRFTnZiblJsYm5RPQ==",
"context_mime" : "text/plain"
},
"location" : {
"accuracy" : "0.564",
"altitude" : "76.2352.3563",
"latitude" : "12.34234.143",
"longitude" : "32.24314.1431"
},
"session_status" : {
"status" : "SUCCESS",
"description" : "Operation has completed successfully",
"state" : "SUCCESS"
},
"risk_attributes" : [ {
"name" : "is_debuggable",
"value" : "true"
}, {
"name" : "is_debugger_connected",
"value" : "true"
}, {
"name" : "input_method",
"value" : "input"
}, {
"name" : "is_emulator",
"value" : "true"
}, {
"name" : "operating_system_version",
"value" : "2.3"
}, {
"name" : "client_side_ip",
"value" : "[\"192.168.0.1\"]"
} ]
}Example response
HTTP/1.1 200 OK3.5. Offline Authentication
An API for doing offline authentications. Offline meaning the device does not have access to the internet. Data is transferred as a verification string to the device (for instance through a QR-code), and verified by a one time password
The offline flow runs as follows:
3.5.1. The offline authentication object
| Field | Type | Description |
|---|---|---|
|
|
The UUID of the authentication session |
|
|
The context used in the authentication |
|
|
String of data transferable to the client to complete the authentication |
|
|
The UUID for the device |
|
|
The time for when the session was created. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The time for when the session will expire. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The authentication method for the operation (Variant 1). See authentication methods for possible values |
|
|
The authentication level of the enrollment. See authentication levels for options |
|
|
Status object that contains status details of the session. See session_status object for details. |
3.5.2. Begin offline authentication
POST /api/smart-device/v1/offline-authentications
To start an offline authentication, you create an offline authentication object
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
The UUID of the device you want to authenticate |
|
|
No |
Amount of time until the authentication will expire in milliseconds |
|
|
No |
Authentication method you want to use (Variant 1). See authentication methods for possible values |
|
|
No |
The context used in the authentication. This must be a UTF-8 String no larger than 300 bytes (length may vary dependent on amount of special characters) |
Example request body
{
"device_id" : "a795def3-3603-4156-bc15-9e901b9834d2",
"context" : "Transaction amount: €2000.-",
"authentication_method" : "OFFLINE_PIN",
"session_expiry_time" : 300000
}Returns
Returns an offline authentication object if authentication process is successfully initiated. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/offline-authentications' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"device_id" : "a795def3-3603-4156-bc15-9e901b9834d2",
"context" : "Transaction amount: €2000.-",
"authentication_method" : "OFFLINE_PIN",
"session_expiry_time" : 300000
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: cac45799-17e0-46e4-873b-6d6d17427dfb
Content-Type: application/json
Content-Length: 591
{
"id" : "1596da56-d0a6-4f59-a837-b16d1ab7db11",
"session_created_time" : "2025-10-28T13:49:57.537UTC",
"session_expiry_time" : "2025-10-28T13:54:57.536UTC",
"session_status" : {
"status" : "IN_PROGRESS",
"description" : "Operation is in progress",
"state" : "IN_PROGRESS"
},
"device_id" : "40570202-0129-4739-9238-0cadd642c54a",
"authentication_method" : "OFFLINE_PIN",
"authentication_level" : "TWO_FACTOR",
"context" : "Transaction amount: €2000.-",
"verification_data" : "1,erZufwhGtGKA/RbdN9BZ4Q,12,VHJhbnNhY3Rpb24gYW1vdW50OiDigqwyMDAwLi0,6,a1f4df35"
}3.5.3. Verify offline authentication
POST /api/smart-device/v1/offline-authentications/{id}/verifications
To verify an offline authentication session, you send in a one-time-password
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
YES |
Client generated OTP to verify |
Example request body
{
"otp" : "123456"
}Returns
Returns the verification status, and the number of remaining attempts if the call is successful. The status can be offline verification status. Returns an error object if something goes wrong.
Response fields
| Field | Type | Description |
|---|---|---|
|
|
The result of the authentication. See offline verification status for possible values. |
|
|
Number of attempts before the authentication method gets locked |
Verification status values
| Status | Description |
|---|---|
|
Operation has completed successfully |
|
Operation failed because the session was cancelled by the device |
|
Operation failed because the session has expired |
|
Operation failed because the device is locked |
|
Operation failed because the authentication method is locked |
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/offline-authentications/ff4a42df-12af-4a01-9102-41df75ce8d28/verifications' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"otp" : "123456"
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: 8b50ebfa-dcdf-410c-8c3a-80f5c0117850
Content-Type: application/json
Content-Length: 54
{
"status" : "FAILURE",
"remaining_attempts" : 2
}3.5.4. Get authentication details
GET /api/smart-device/v1/offline-authentications/{id}
Getting the authentication session details lets you know the state of the authentication and all other attributes created as part of the offline-authentication process.
Returns
Returns an offline authentication object if a valid identifier was provided, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/offline-authentications/47620f50-e71a-42d6-8337-61349bd5b7c9' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: e88ee8e4-c4b2-42a1-b310-c43f0050b4bc
Content-Type: application/json
Content-Length: 591
{
"id" : "60c129ac-e5e2-49bc-a927-390d7c558b14",
"session_created_time" : "2025-10-28T13:49:57.924UTC",
"session_expiry_time" : "2025-10-28T13:54:57.924UTC",
"session_status" : {
"status" : "IN_PROGRESS",
"description" : "Operation is in progress",
"state" : "IN_PROGRESS"
},
"device_id" : "f7b4b016-2ac7-4c6d-b3c7-64d1b56a6c95",
"authentication_method" : "OFFLINE_PIN",
"authentication_level" : "TWO_FACTOR",
"context" : "Transaction amount: €2000.-",
"verification_data" : "1,6T99YUO+oPIumAj4+fWkyw,12,VHJhbnNhY3Rpb24gYW1vdW50OiDigqwyMDAwLi0,6,47f54755"
}3.5.5. Cancel authentication
DELETE /api/smart-device/v1/offline-authentications/{id}
To cancel an authentication session in progress thereby preventing the device from finishing the authentication process
Returns
Returns an empty response if the operation succeeds. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/offline-authentications/48d07c93-d73c-4693-b6e6-a343ed9b6ed6' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: 166efc44-3017-4ee1-a039-fdf626d16bbf3.6. Device
Each successful enrollment process registers a new device, this API can retrieve details for a device and deactivate it.
3.6.1. The device object
| Field | Type | Description |
|---|---|---|
|
|
The UUID for the device |
|
|
The application ID for the device |
|
|
The client API version used in the device’s last operation |
|
|
The client API version that the device was originally activated on |
|
|
Encap server release version that the device was originally activated on |
|
|
SHA256 hash of the unique hardware device ID of the client device. |
|
|
SHA256 hash of the device client salt. |
|
|
The operating system type of the device |
|
|
The device manufacturer |
|
|
The device model |
|
|
List of activated authentication methods (Variant 2). See authentication methods for possible values |
|
|
The time for when the device was originally activated |
|
|
The time for when the device last made an operation |
|
|
An lock object containing lock details. Only present when the device is locked |
|
|
The reference url for the lock |
|
|
List containing all reasons for the device lock. See lock reason for possible values. |
|
|
The push address for the device, this address is used when sending push to the device using FCM or APNS. |
|
|
List of all recoveries for the device. See recovery object for details. |
|
|
Explicit setting for the device to lock/unlock recovery. |
|
|
Attestation object that contains details for all the attestations performed for the device. See attestation object for details. |
3.6.2. Get device details
GET /api/smart-device/v1/devices/{deviceId}
Get device details
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 597a893d-c4cc-43c3-8bb8-9aa11e05805c
Content-Type: application/json
Content-Length: 1510
{
"id" : "e8f8159d-9974-4e18-89a8-be64996632e6",
"application_id" : "encap",
"current_client_api_version" : "3.21.0",
"activated_client_api_version" : "3.21.0",
"activated_encap_release" : "R_3_21",
"device_hash" : "Xsx6d7bmhh9ovUvhqp5KLOs480%2FWCq3bq9%2FC0apC4TU%3D",
"salt_hash" : "ap7cmrQQTc0zb5aCPgXV0JxvrFeOO6CguQklentLMsc%3D",
"push_address" : "ap7cmrQQTc0zb5aCPgXV0JxvrFeOO6CguQklentLMsc",
"operating_system_type" : "iOS",
"device_manufacturer" : "Apple",
"device_model" : "iPhone14,2",
"activated_authentication_methods" : [ "DEVICE", "DEVICE:PIN" ],
"activation_time" : "2017-04-05T12:23:00.000UTC",
"last_used_time" : "2025-10-28T13:49:59.232UTC",
"lock" : {
"ref" : "/devices/f13921f9-b4ae-4760-86fc-2bba8c0ab118/lock",
"lock_reason" : [ "DEVICE_VERIFICATION_FAILED", "LOCKED_BY_ADMIN" ]
},
"attestation" : {
"safety_net_status" : "VERIFIED",
"safety_net_date" : "2025-10-28T13:49:59.232UTC",
"app_attest_status" : "VERIFIED",
"app_attest_date" : "2025-10-28T13:49:59.232UTC",
"play_integrity_status" : "VERIFIED",
"play_integrity_date" : "2025-10-28T13:49:59.232UTC"
},
"recoveries" : [ {
"recovery_id" : "990fffe0-1454-4110-ac82-87211f87e211",
"recovery_method" : "CLOUD_BACKUP_RECOVERY_CODE",
"recovery_status" : "ACTIVATED",
"created_date" : "2025-10-28T13:49:59.232UTC",
"updated_date" : "2025-10-28T13:49:59.232UTC",
"recovered_date" : "2025-10-28T13:49:59.232UTC"
} ],
"recovery_lock" : false
}3.6.3. Deactivate device
DELETE /api/smart-device/v1/devices/{deviceId}
Disable authentication credentials for this device. This includes deleting device credentials.
Returns
Returns 204 No Content if a valid identifier was provided and the device was deleted. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: 81793a31-ceb2-4823-a978-c58cc91d02493.7. Device Sessions
All operations for a given enrollment creates a session. A list of all sessions for a device can be retrieved including some meta info for each session. For a more detailed description of a session follow the detailed link in the meta info for that session. For sessions with an operation type without a REST API, the detail link is omitted.
3.7.1. The session object
| Field | Type | Description |
|---|---|---|
|
|
The UUID for the session |
|
|
Link to authentication object for the session |
|
|
The purpose of the session. See session purpose for details. |
|
|
The state of the session |
|
|
The date for when the session was created. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The date for when the session expires. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
True if this is an offline authentication session |
|
|
True if the session was run in client only mode |
|
|
The device ID that owns the session |
3.7.2. Get sessions for device
GET /api/smart-device/v1/device/{deviceId}/sessions?limit=10&offset=0
Returns
Returns a pagination object with a list of session objects if a valid identifier was provided, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/sessions?limit=5' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 43893c55-3f63-436c-a956-bf8dfd67e719
Content-Type: application/json
Content-Length: 1488
{
"previous" : "/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/sessions?limit=5&offset=cd4e1f77-5b69-41fb-baba-370025c1512b",
"next" : "/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/sessions?limit=5&offset=893bfacd-7bbf-4a9a-bd3b-657d0212102a",
"limit" : 5,
"items" : [ {
"session_id" : "fff6bb76-1853-4ca4-a432-6a718b7b5dd8",
"device_id" : "73a7919e-733c-41aa-b3a8-7820d0d7d0c0",
"ref" : "/enrollments/fff6bb76-1853-4ca4-a432-6a718b7b5dd8",
"purpose" : "ACTIVATION",
"state" : "SUCCESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:57.575UTC",
"session_expires_on" : "2025-10-28T13:49:57.575UTC",
"offline" : false
}, {
"session_id" : "f59f24a3-c68b-4562-8571-ee411cb983a7",
"device_id" : "73a7919e-733c-41aa-b3a8-7820d0d7d0c0",
"ref" : "/authentications/f59f24a3-c68b-4562-8571-ee411cb983a7",
"purpose" : "AUTHENTICATION",
"state" : "IN_PROGRESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:57.575UTC",
"session_expires_on" : "2025-10-28T13:49:57.575UTC",
"offline" : false
}, {
"session_id" : "ed724c36-f532-47ee-90ac-8180e78ce459",
"device_id" : "73a7919e-733c-41aa-b3a8-7820d0d7d0c0",
"purpose" : "DELETE_RECOVERY",
"state" : "IN_PROGRESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:57.575UTC",
"session_expires_on" : "2025-10-28T13:49:57.575UTC",
"offline" : false
} ]
}3.8. Sessions for multiple devices
Retrieve a list of the latest sessions for a set of devices, including limited meta info for each session. Follow the reference link in the meta info for more detailed description of the session and its meta info. For sessions with an operation type without a REST API, the reference link is omitted. The number of devices to query is limited to 100.
3.8.1. Get sessions for multiple devices
GET /api/smart-device/v1/sessions/sessions?deviceId={deviceId1}&deviceId={deviceId2}&limit=10&offset=0
Returns
Returns a pagination object with a list of session objects if all identifiers are valid, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/sessions?deviceId=8e122d40-2868-4609-9d64-502b4ca5ed8a&deviceId=3cb92dad-6d6e-49ef-b953-32780d7b340e&limit=4' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 6272d901-d8ec-44d4-b79d-fc3097fe39ed
Content-Type: application/json
Content-Length: 2057
{
"previous" : "/smart-device/v1/sessions?deviceId=8e122d40-2868-4609-9d64-502b4ca5ed8a&deviceId=3cb92dad-6d6e-49ef-b953-32780d7b340e&limit=4&offset=75f6889f-31ad-420c-8b2b-965db886f127",
"next" : "/smart-device/v1/sessions?deviceId=8e122d40-2868-4609-9d64-502b4ca5ed8a&deviceId=3cb92dad-6d6e-49ef-b953-32780d7b340e&limit=4&offset=f81f513b-da5a-4848-864d-8b89a70eeacb",
"limit" : 4,
"items" : [ {
"session_id" : "e85c453f-ecc0-4d6c-9699-c626964c3ef0",
"device_id" : "a3c5e3ed-30da-40f1-a0e6-2c64694648f0",
"ref" : "/enrollments/e85c453f-ecc0-4d6c-9699-c626964c3ef0",
"purpose" : "ACTIVATION",
"state" : "SUCCESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:55.356UTC",
"session_expires_on" : "2025-10-28T13:49:55.356UTC",
"offline" : false
}, {
"session_id" : "e9c30454-f226-4b00-851a-f5c2bdfd0b36",
"device_id" : "a3c5e3ed-30da-40f1-a0e6-2c64694648f0",
"ref" : "/authentications/e9c30454-f226-4b00-851a-f5c2bdfd0b36",
"purpose" : "AUTHENTICATION",
"state" : "IN_PROGRESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:55.356UTC",
"session_expires_on" : "2025-10-28T13:49:55.356UTC",
"offline" : false
}, {
"session_id" : "91ea94b0-abd9-4e7f-ae15-d07574349e0f",
"device_id" : "9c8c6f64-a069-4fe1-a8a0-c376de3887b6",
"ref" : "/enrollments/91ea94b0-abd9-4e7f-ae15-d07574349e0f",
"purpose" : "ACTIVATION",
"state" : "SUCCESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:55.356UTC",
"session_expires_on" : "2025-10-28T13:49:55.356UTC",
"offline" : false
}, {
"session_id" : "a966a32e-7ea6-4610-909e-49870def8b06",
"device_id" : "9c8c6f64-a069-4fe1-a8a0-c376de3887b6",
"ref" : "/authentications/a966a32e-7ea6-4610-909e-49870def8b06",
"purpose" : "AUTHENTICATION",
"state" : "IN_PROGRESS",
"client_only" : false,
"session_created_on" : "2025-10-28T13:49:55.356UTC",
"session_expires_on" : "2025-10-28T13:49:55.356UTC",
"offline" : false
} ]
}3.9. Device Lock
Every device can have a lock. A lock can be created through this API or as a result of various other processes.
3.9.1. The lock object
| Field | Type | Description |
|---|---|---|
|
|
The UUID for the device |
|
|
An lock object containing lock details |
|
|
The reference url for the lock |
|
|
List containing all reasons for the device lock. See lock reason for possible values. |
3.9.2. Lock device
POST /api/smart-device/v1/devices/{deviceId}/lock
A device is locked by creating a lock on the device-id.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/lock' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POSTExample response
HTTP/1.1 200 OK
X-Correlation-UUID: caf3f2ce-abe5-4827-996e-9a8b87bd5d74
Content-Type: application/json
Content-Length: 207
{
"id" : "e8f8159d-9974-4e18-89a8-be64996632e6",
"lock" : {
"ref" : "/devices/e8f8159d-9974-4e18-89a8-be64996632e6/lock",
"lock_reason" : [ "DEVICE_VERIFICATION_FAILED", "LOCKED_BY_ADMIN" ]
}
}3.9.3. Get lock status for device
GET /api/smart-device/v1/devices/{deviceId}/lock
Looking at the lock for a device-id will tell why the device was locked.
Returns
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/lock' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 137de22d-5473-4452-bc68-f672c9b6be33
Content-Type: application/json
Content-Length: 207
{
"id" : "e8f8159d-9974-4e18-89a8-be64996632e6",
"lock" : {
"ref" : "/devices/e8f8159d-9974-4e18-89a8-be64996632e6/lock",
"lock_reason" : [ "DEVICE_VERIFICATION_FAILED", "LOCKED_BY_ADMIN" ]
}
}3.9.4. Unlock device
DELETE /api/smart-device/v1/devices/{deviceId}/lock
A device is unlocked by removing the lock from the device-id.
Returns
Returns 204 No Content if a valid identifier was provided and lock was removed. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/lock' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: 5de08472-be22-4540-9719-76153c273b583.10. Lock authentication method
In addition to devices, every authentication method can have a lock. A locked offline-method does not result in the entire device being locked. While locking an online-method will lock the device and make it unable to perform any operation.
See authentication methods for possible values for authMethod (Variant 1).
3.10.1. Lock authentication method
POST /api/smart-device/v1/devices/{deviceId}/authmethods/{authMethod}/lock
Locks the specified authentication method for the device.
Returns
Returns an empty response if the operation succeeds. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/33052ceb-3d0c-4183-85d7-91888c182b1d/authmethods/OFFLINE_PIN/lock' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POSTExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: 13094bdc-d54c-4669-bec6-69fa58baf8a93.10.2. Get the lock status for the authentication method of the device.
GET /api/smart-device/v1/devices/{deviceId}/authmethods/{authMethod}/lock
Fetches the lock status of the specified authentication method.
Returns
Returns the lock status of the authentication method.
| Field | Type | Description |
|---|---|---|
|
|
Lock status of this auth method |
Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/cbec6ab5-3d3a-408b-97ee-b835234183b7/authmethods/OFFLINE_PIN/lock' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 1b55a648-94c2-4e6f-b656-dd3b086f0eda
Content-Type: application/json
Content-Length: 39
{
"lock_status" : "LOCKED_BY_ADMIN"
}3.10.3. Get the lock status for all authentication methods of the device.
GET /api/smart-device/v1/devices/{deviceId}/authmethods
Gets the lock status for each authentication method that the device has.
Returns
Returns all authentication methods with lock status.
{
"authentication_methods" : [ {
"auth_method" : "DEVICE",
"lock_status" : "OPEN"
}, {
"auth_method" : "DEVICE_PIN",
"lock_status" : "PIN_VERIFICATION_FAILED"
}, {
"auth_method" : "DEVICE_ANDROID_BIOMETRIC_PROMPT",
"lock_status" : "OPEN"
} ]
}Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/c67277cc-00bd-44fc-a0c1-e64b99dbbc98/authmethods' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: bdca5a13-da78-4edc-a978-521d5a760868
Content-Type: application/json
Content-Length: 275
{
"authentication_methods" : [ {
"auth_method" : "DEVICE",
"lock_status" : "OPEN"
}, {
"auth_method" : "DEVICE_PIN",
"lock_status" : "PIN_VERIFICATION_FAILED"
}, {
"auth_method" : "DEVICE_ANDROID_BIOMETRIC_PROMPT",
"lock_status" : "OPEN"
} ]
}3.10.4. Unlock authentication method
DELETE /api/smart-device/v1/devices/{deviceId}/authmethods/{authMethod}/lock
Removes the lock from the authentication method.
Returns
Returns 204 No Content if successful. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/52d0b5ab-4ba1-442b-87af-dde7fe850c5e/authmethods/OFFLINE_PIN/lock' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: cb6896c4-7d4c-41fa-9e07-cad25442e4013.11. Account Recovery
Account Recovery adds support for recovering a device after it being replaced, lost or stolen. With Account Recovery the user can add recovery for his device that is protected with a user created recovery code (PIN). The recovery secret is stored in the cloud backup (Google Cloud or Apple iCloud) provided that the user has enabled backup of his apps. The feature allows the user to recover the app on another device while the service provider reference (device_id) remains unchanged.
3.11.1. The perform recovery session object
| Field | Type | Description |
|---|---|---|
|
|
The UUID for the recovery session |
|
|
The application ID for the device |
|
|
The UUID for the device |
|
|
The time for when the session was created. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The time for when the session will expire. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The purpose of the session. See session purpose for details. |
|
|
List of activated authentication methods (Variant 2). See authentication methods for possible values |
|
|
The recovery method used to set up the recovery. |
|
|
The recovery status of a given recovery. |
|
|
List that contains name and value for all risk attributes. See risk_attributes object for details. |
|
|
Location object that contains location details, see location object for details. |
|
|
Status object that contains status details of the session. See session_status object for details. |
|
|
Attestation object that contains details for all the attestations performed for the device. See attestation object for details. |
3.11.2. Get perform recovery details
GET /api/smart-device/v1/perform-recoveries/{session_id}
Get the session details after performing a recovery. The session details let you know the state of the recovery, and if finished it gives you access to risk data and all other attributes created as part of the recovery process. You can find the session_id by looking at the device sessions with the correct session purpose.
Returns
Returns an perform recovery object if a valid session identifier was provided, otherwise returns an error.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/perform-recoveries/de2455f0-5f36-416d-bf97-0f02aff7cefd' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: cb4943a2-fbc5-4020-bb0b-1174cd070fd2
Content-Type: application/json
Content-Length: 1435
{
"id" : "de2455f0-5f36-416d-bf97-0f02aff7cefd",
"application_id" : "encap",
"device_id" : "49e4ca35-f551-4fc5-86f4-365567328392",
"session_created_time" : "2025-10-28T13:49:56.401UTC",
"session_expiry_time" : "2025-10-28T15:49:56.401UTC",
"activated_authentication_methods" : [ "DEVICE", "DEVICE:PIN" ],
"location" : {
"accuracy" : "0.564",
"altitude" : "76.2352.3563",
"latitude" : "12.34234.143",
"longitude" : "32.24314.1431"
},
"risk_attributes" : [ {
"name" : "is_debuggable",
"value" : "true"
}, {
"name" : "is_debugger_connected",
"value" : "true"
}, {
"name" : "input_method",
"value" : "input"
}, {
"name" : "is_emulator",
"value" : "true"
}, {
"name" : "operating_system_version",
"value" : "2.3"
}, {
"name" : "client_side_ip",
"value" : "[\"192.168.0.1\"]"
} ],
"session_status" : {
"status" : "IN_PROGRESS",
"description" : "Operation is in progress",
"state" : "IN_PROGRESS"
},
"attestation" : {
"safety_net_status" : "VERIFIED",
"safety_net_date" : "2025-10-28T13:49:56.400UTC",
"app_attest_status" : "VERIFIED",
"app_attest_date" : "2025-10-28T13:49:56.400UTC",
"play_integrity_status" : "VERIFIED",
"play_integrity_date" : "2025-10-28T13:49:56.400UTC"
},
"purpose" : "PERFORM_RECOVERY",
"recovery_method" : "CLOUD_BACKUP_SERVER_SIDE_FACE",
"recovery_status" : "ACTIVATED"
}3.12. Recovery Lock for device
The Account Recovery feature is enabled in the application configuration and can by default be used by all devices. The feature can be disabled for an explicit device by setting the recovery lock using this API, or by setting the recovery lock field when doing a new enrollment.
The recovery lock is by default set to false and if set to true the device will not be able to perform any recovery operations.
3.12.1. The recovery lock object
| Field | Type | Description |
|---|---|---|
|
|
Explicit setting for the device to lock/unlock recovery. |
3.12.2. Get recovery lock status for device
GET /api/smart-device/v1/devices/{deviceId}/recovery-lock
Check if recovery is locked for the given device
Returns
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/recovery-lock' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 2d26aeb1-831c-49e6-b6e4-f6384d498f01
Content-Type: application/json
Content-Length: 29
{
"recovery_lock" : false
}3.12.3. Change recovery lock
PUT /api/smart-device/v1/devices/{deviceId}/recovery-lock
Lock/unlock recovery for the given device
Returns
Returns 202 Accepted if setting the recovery lock is successful. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/recovery-lock' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X PUT \
-H 'Content-Type: application/json' \
-d '{
"recovery_lock" : "true"
}'Example response
HTTP/1.1 202 Accepted
X-Correlation-UUID: 967305fc-82a8-42ed-8705-e92be87dd36e
Content-Type: application/json
Content-Length: 28
{
"recovery_lock" : true
}3.13. Override Geofencing settings for device
The Geofencing feature is configured in the application configuration and by default the settings therein applies to all devices. The geofencing configuration for authentication operations can be overridden for an explicit device using this API. By overriding the configuration, the device will have a fully independent configuration (for authentication operations), and the settings in application configuration will no longer apply.
3.13.1. The geofencing object
| Field | Type | Description |
|---|---|---|
|
|
Geofencing enforcement mode (OFF/OPTIONAL/REQUIRED) |
|
|
Comma separated list of continents in which authentication is allowed (AF/NA/OC/AN/AS/EU/SA) |
|
|
Comma separated list of countries in which authentication is allowed (in addition to allowed continents). ISO 3166-1 alpha-2 standard. |
|
|
Comma separated list of countries in which authentication is not allowed (exception from allowed continents). ISO 3166-1 alpha-2 standard. |
3.13.2. Get geofencing configuration for device
GET /api/smart-device/v1/devices/{deviceId}/geofencing
Retrieve geofencing configuration for the given device
Returns
Returns a geofencing object if a valid device identifier is provided. Returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/geofencing' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 0f980b34-91a2-45eb-ac0b-b9d732c0f349
Content-Type: application/json
Content-Length: 115
{
"mode" : "OPTIONAL",
"allowed_continents" : "EU",
"allowed_countries" : "CT",
"denied_countries" : "RU"
}3.13.3. Update geofencing configuration for device
PUT /api/smart-device/v1/devices/{deviceId}/geofencing
Update geofencing configuration for the given device
Returns
Returns 202 Accepted together with the updated geofencing object if the update is successful. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/geofencing' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X PUT \
-H 'Content-Type: application/json' \
-d '{
"mode" : "OPTIONAL",
"allowed_continents" : "EU",
"allowed_countries" : "CT",
"denied_countries" : "RU"
}'Example response
HTTP/1.1 202 Accepted
X-Correlation-UUID: f41a2fee-0cb7-465d-ad74-888990f13025
Content-Type: application/json
Content-Length: 115
{
"mode" : "OPTIONAL",
"allowed_continents" : "EU",
"allowed_countries" : "CT",
"denied_countries" : "RU"
}3.13.4. Delete geofencing configuration for device
DELETE /api/smart-device/v1/devices/{deviceId}/geofencing
Delete geofencing configuration for the given device
Returns
Returns 204 No Content if successful. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/smart-device/v1/devices/e8f8159d-9974-4e18-89a8-be64996632e6/geofencing' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: c46dfa6a-b3f2-4e45-bd8e-518aeb8dd0d54. Admin API
4.1. Server status
Provides a health check of the Encap instances. If called unauthenticated only a overall status is provided.
4.1.1. The status object
| Field | Type | Description |
|---|---|---|
|
|
Indicates if the API is in a "healthy" state |
|
|
An RFC 3339 formatted date and time in UTC |
|
|
Array of underlying dependencies and their status. Only included if request is authenticated |
|
|
Indicates if this dependency is in a "healthy" state |
|
|
Time in milliseconds it took to check this dependency |
|
|
Name of dependency |
4.1.2. Get API status
GET /api/admin/v1/status
Example request
$ curl 'http://localhost:8080/api/admin/v1/status' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: d403051c-3e1c-4500-9d3b-a7d0fb6cbf79
Content-Type: application/json
Content-Length: 179
{
"success" : true,
"created_on" : "2025-10-28T13:49:53.678UTC",
"dependencies" : [ {
"resource" : "Core database",
"success" : true,
"request_time" : 10
} ]
}Example response if unauthenticated
HTTP/1.1 200 OK
X-Correlation-UUID: 98c90d9c-0958-491d-9256-6287fdc2945b
Content-Type: application/json
Content-Length: 93
{
"success" : true,
"created_on" : "2025-10-28T13:49:54.177UTC",
"dependencies" : [ ]
}4.2. Application Configuration
Operations on Application Configuration.
Consult 3.1.2 - ApplicationID configurations in the Encap Server Administration Manual for information about this topic.
All operations on this endpoint requires authentication. See the rest api authentication section
4.2.1. The application configuration object
| Field | Type | Description |
|---|---|---|
|
|
The logical name of the application configuration |
|
|
The unique ID of this application configuration registration. This value is central to these APIs |
|
|
Reference to the APNS push certificate or token. |
|
|
The human readable name for the application configuration |
|
|
The application configuration parameters |
4.2.2. The configuration object
This object contains the configuration parameters and their value
| Parameter | Description | Allowed values | Default |
|---|---|---|---|
|
Lower limit for how guessable the activation code is. Given as 1 in x where this param represents x. The server calculates the actual value based on the cardinality of the activation code type, the activation code length and the number of active activations. If this value is below 1 in x with x as defined here the server prevents the new activation from starting. It is not possible to set this lower than 1 in 1,000. The higher the number the lower the probability is of guessing the activation code. To increase the number of concurrently active activation supported increase the ACTIVATION_CODE_LENGTH or choose a ACTIVATION_CODE_TYPE with greater cardinality. E.g. ACTIVATION_CODE_LENGTH = 4 ACTIVATION_CODE_TYPE = NUMERIC This gives 10,000 possible activation codes. With 1 activation in progress the chance of guessing the activation code is 1 in 10,000. With 10 concurrent activations we have a chance of guessing a valid code reduced to 1 in 1,000 (10,000 / 10 = 1,000). If an 11th activation session starts before any of the others finish it will fail the ACTIVATION_CODE_ALLOWED_GUESS_PROBABILITY check as this brings the chance below 1 in 1,000 (10,000 / 11 = 909). |
1000 .. MAXINT |
1000 |
|
The length in characters of the activation code that should be generated. |
4 .. MAXINT |
6 |
|
The type of characters that can be used during the generation of the activation code. |
ALPHA, ALPHANUMERIC, ANY, NUMERIC |
NUMERIC |
|
Comma separated list of allowed authentication methods. Determines which auth methods can be activated and used for authentication |
See authentication methods for applicable auth methods (Variant 1) |
DEVICE, DEVICE:PIN |
|
Comma separated list of allowed authentication methods for activation of a new auth-method. Determines which auth methods can be used to authenticate during activation of a new auth method. The value(s) here must be present in the ALLOWED_AUTH_METHODS parameter. Offline authentication methods can not be used here. |
See authentication methods for applicable auth methods (Variant 1) |
DEVICE:PIN |
|
The grace amount of failed DEVICE_PIN (or offline) authentications for any client before they are locked out. |
0..MAXINT |
3 |
|
The APN server configuration that defines where to reach the APNs. |
PRODUCTION, SANDBOX |
PRODUCTION |
|
The expiration time for an APNs message, set in milliseconds, indicates how long APNs should try to deliver the message. If not delivered by this time, the message is discarded, although APNs attempts delivery at least once regardless of the expiration time. |
0..MAXINT |
86400000 |
|
Apples bundle id for the application. Used as topic on the push message sent to APNs, required when using APNs provider token for sending push messages. |
String |
|
|
Enable notification sound for push messages to iOS devices. |
true, false |
false |
|
Sets the interruption level for push messages to iOS devices to "time-sensitive". |
true, false |
false |
|
True if the client is allowed to perform client-only activations and authentications. A client-only operation is one that is not initiated by a service provider request. |
true, false |
true |
|
Android SDK API versions to blacklist (and reject). See the android configuration chapter in the server manual for smart device for details. |
Comma separated semantic version, ex: "3.5.3, 3.6.8" |
null |
|
IOS SDK API versions to blacklist (and reject). See the ios configuration chapter in the server manual for smart device for details. |
Comma separated semantic version, ex: "3.5.3, 3.6.8" |
null |
|
Comma separated list of which risk data to store, or ALL if all the available risk data should be stored. Details for risk data is specified in the EncapAuthenticationStateless document and in the REST documentation. |
See config attribute column in risk_attributes for available values. Value 'ALL' will enable all risk attributes. |
Default value is empty which represents that no risk data is enabled. |
|
Firebase Cloud Messaging. The contents of the serviceAccount.json (credentials file) for your Firebase Cloud Messaging project. |
String |
|
|
Firebase Cloud Messaging. Maximum lifespan of the message in milliseconds. The default value is 0. This means deliver “now or never”. FCM guarantees best effort for messages with this lifespan. Maximum duration is 4 weeks. |
0..MAXINT |
0 |
|
What to do if validating the signature based on the hardware supported keys. SUPPORTED means that clients who register the public key in a healthy manner during Registration, will fail Authentication if they fail to provide a signature based on the Hardware Supported key. If this flag is RISK_PARAMS, the failing signature will only result in risk parameters on authentication and will not fail the authentication. |
SUPPORTED RISK_PARAMS |
SUPPORTED |
|
The amount of time (in milliseconds) that a new client session remains valid for. After this time has elapsed, the session can no longer be used for any operations |
1..MAXINT |
300000 |
|
The maximum amount of time (in milliseconds) the sessionExpiry can be set to. |
1..MAXINT |
300000 |
|
What Android client SDK version should be allowed. This can be used to narrow (not extend) the SDK version. Example is if the server minimum is "3.15.0", and someone wants to only allow "3.16.0" -clients, this can be achieved here. But putting "3.13.0" will not have any effect. |
Semantic version, ex: "3.17.0" |
null |
|
The same as MINIMUM_REQUIRED_ENCAP_API_VERSION_ANDROID, but applies to iOS clients. |
Semantic version, ex: "3.17.0" |
null |
|
Enable the server to send push messages with Fire Cloud Messaging or Apple APNS |
true, false |
false |
|
Enable users to set up recovery with an alternative set of user credentials |
true, false |
false |
|
The minimum number of characters for the recovery PIN. Note: This is a hint to the client and not enforced by the server. |
0..MAXINT |
6 |
|
The maximum number of characters for the recovery PIN. Note: This is a hint to the client and not enforced by the server. |
0..MAXINT |
50 |
|
The type of characters that can be used in the recovery PIN. Note: This is a hint to the client and not enforced by the server. |
ALPHA, ALPHANUMERIC, ANY, NUMERIC |
NUMERIC |
|
The grace amount of failed recovery code attempts for any client before the recovery for the client is locked. |
0..MAXINT |
3 |
|
Authorization token timeout in milliseconds. After this time, the token will not be valid anymore. |
0..MAXINT |
300000 |
|
Geofencing mode for activation. REQUIRED: Device location check is performed. If the location is not part of the allowed regions or the location check fails, activation request will fail. OPTIONAL: Device location check is performed. If the location is not part of the allowed regions or the location check fails, activation request will be performed and Service Provider will be notified about it via the API. OFF: Device location check is not performed. |
REQUIRED, OPTIONAL, OFF |
OFF |
|
List of continents in which activation is allowed. |
2 letter continent codes (AF/NA/OC/AN/AS/EU/SA), in a comma separated list. |
|
|
List of countries in which activation is allowed in addition to allowed continents. |
Country codes following ISO 3166-1 alpha-2 standard, in a comma separated list. |
|
|
List of countries in which activation is not allowed (exception from allowed continents). |
Country codes following ISO 3166-1 alpha-2 standard, in a comma separated list. |
|
|
Geofencing mode for authentication. REQUIRED: Device location check is performed. If the location is not part of the allowed regions or the location check fails, authentication request will fail and Service Provider will be notified about it via the API. OPTIONAL: Device location check is performed. If the location is not part of the allowed regions or the location check fails, authentication request will be performed. OFF: Device location check is not performed. |
REQUIRED, OPTIONAL, OFF |
OFF |
|
List of continents in which authentication is allowed. |
2 letter continent codes (AF/NA/OC/AN/AS/EU/SA), in a comma separated list. |
|
|
List of countries in which authentication is allowed in addition to allowed continents. |
Country codes following ISO 3166-1 alpha-2 standard, in a comma separated list. |
|
|
List of countries in which authentication is not allowed (exception from allowed continents). |
Country codes following ISO 3166-1 alpha-2 standard, in a comma separated list. |
|
|
Timeout allowed for the client to wait for location and perform reverse geolocation lookup (if the timeout is exceeded, the client will continue without country). |
0..MAXINT |
10000 |
|
Comma separated list of events that shall trigger a REST callback to the service provider url configured. You can also filter events per API to have even more control of when a callback should be issued. Allowed events: See event-callback-events When not specifying an API the callback for the event will be sent regardless of API. e.g. DEVICE_LOCKED, DEVICE_DEACTIVATED:[REST] Format specification: <event-type-1>[:< [api-1|api-2|…] >], <event-type-2>[:< [api-1|api-2|…] >] |
Allowed events: See event-callback-events |
|
|
The URL that should receive callbacks in case any callback events have been configured for this app-config. |
String |
|
|
Comma separated list of operating system types (iOS/Android) for enabling client debug data. It might be set to one of the platforms, or both. It is empty by default, hence no client debug data is sent to the server. |
IOS, ANDROID |
|
|
The minimum length in characters of the PIN. Note: This is a hint to the client and not enforced by the server (but enforced in the client SDK). |
1..MAXINT |
4 |
|
The maximum length in characters of the PIN. Note: This is a hint to the client and not enforced by the server (but enforced in the client SDK). |
1..MAXINT |
4 |
|
The type of characters that can be used in the PIN. Note: This is a hint to the client and not enforced by the server. |
ANY, NUMERIC, ALPHA, ALPHANUMERIC |
NUMERIC |
|
The type of token to respond with to the client when one is requested. Note: The client can request a different type of token during the authentication operation. This setting indicates the default type to use when the client doesn’t specify one. |
SAML1, SAML2 |
SAML2 |
|
The scheme part of URLs generated for push methods that require a URL. This is the URL Scheme that the client is configured to be activated with. |
A valid URL scheme |
encap |
|
SafetyNet Attestation mode. REQUIRED: SafetyNet attestation is preformed. If attestation fails activation/authentication request will fail. OPTIONAL: SafetyNet attestation is preformed. If attestation fails activation/authentication request will not fail and a new attestation is performed on the next request. OFF: SafetyNet attestation is not preformed. The SafetyNet API has been deprecated by Google and is now replaced by the Play Integrity API which is supported from Encap 3.17. |
REQUIRED, OPTIONAL, OFF |
OFF |
|
SafetyNet Attestation integrity mode. Defines the strictness when interpreting the SafetyNet attestation. Required if ATTESTATION_ANDROID_SAFETYNET_MODE is REQUIRED or OPTIONAL. LEAN: Requires basicIntegrity integrity to be true. STRICT: Requires both ctsProfileMatch and basicIntegrity to be true. |
LEAN, STRICT |
|
|
SafetyNet Attestation timeout, in milliseconds, the timeout for a request made to SafetyNet. Required if ATTESTATION_ANDROID_SAFETYNET_MODE is REQUIRED or OPTIONAL. |
1..MAXINT |
|
|
Play Integrity attestation mode. REQUIRED: Play Integrity attestation is preformed. If attestation fails activation/authentication request will fail. OPTIONAL: Play Integrity attestation is preformed. If attestation fails activation/authentication request will not fail and a new attestation is performed on the next request. OFF: Play Integrity attestation is not preformed. Play Integrity attestation was introduced in version 3.17 and will only be applicable for clients 3.17 or newer. |
REQUIRED, OPTIONAL, OFF |
OFF |
|
Play Integrity attestation timeout, in milliseconds, the timeout for a request made to Play Integrity. Required if ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE is REQUIRED or OPTIONAL. |
1..MAXINT |
|
|
Play Integrity attestation decryption key, used to decrypt the integrity token. Required if ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE is REQUIRED or OPTIONAL. |
Base64 |
|
|
Play Integrity attestation verification key, used to validate the integrity token. Required if ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE is REQUIRED or OPTIONAL. |
Base64 |
|
|
Play Integrity/SafetyNet attestation, the APK package name. Required if ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE or ATTESTATION_ANDROID_SAFETYNET_MODE is REQUIRED or OPTIONAL. |
String |
|
|
SafetyNet Attestation, the APK certificate SHA-256 digest. Base64 encoded SHA-256. Required if ATTESTATION_ANDROID_SAFETYNET_MODE is REQUIRED or OPTIONAL. |
Base64 |
|
|
iOS Attestation mode when using Apple App Attest. REQUIRED: App attestation enabled. If attestation fails the activation/authentication request will fail. Note that devices running versions of iOS older than 14 will always fail if the mode is set to REQUIRED, due to requirements by the Apple App Attest API. OPTIONAL: App attestation enabled. Even if the attestation fails, the activation/authentication request will succeed, and a new attestation will be performed on the next request. The status can be seen in the response object. OFF: App attestation disabled. |
REQUIRED, OPTIONAL, OFF |
OFF |
|
The environment for an app that uses the App Attest service to validate itself. |
DEVELOPMENT, PRODUCTION |
PRODUCTION |
|
iOS app attestation timeout, after this time, in milliseconds, the attestation request will time out. |
1..MAXINT |
20000 |
|
App ID which is a concatenation of a 10-digit team identifier, a period, and the app’s CFBundleIdentifier value. Required when using Apple App Attest service. |
String |
|
|
Validation of client request time to be able to block client requests coming in to the server out of order. Recommending to set as enabled, and should only be disabled in case of an error or for debugging purposes. |
true, false |
true |
|
Perform validation of the client request time if the new request is within the threshold time of the last one. Recommended to set equal or higher to the load balancer idle timeout. |
1..MAXINT |
300000 |
|
Length of one time password. Required if any of the OTP authentication methods are available. |
4..9 |
|
|
This setting determines the lock behavior following failed authentication attempts. AUTH_METHOD: Only the current auth method will be locked. This allows the user to unlock it using another valid, unlocked method. DEVICE: The entire device will be locked, rendering all authentication methods unusable. In this case, the service provider must unlock the device using the device admin REST API. |
AUTH_METHOD, DEVICE |
AUTH_METHOD |
|
Server Side Face OAuth2 credentials. The base64 encoded clientId:clientSecret provided when signing up for Server Side Face feature |
Base64 |
4.2.3. Create application configuration
POST /api/admin/v1/appconfig
Creates a new application configuration. Returns the application configuration object.
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
The logical name of the application configuration |
|
|
No |
The UUID of the APNs push certificate or token used. Required if NATIVE_PUSH_ENABLED is true. |
|
|
No |
The human readable name for the application configuration |
|
|
Yes |
The application configuration parameters. Required to contain at least one configuration. |
Returns
Returns an application configuration object if request is process successfully. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/admin/v1/appconfig' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"app_id" : "some-new-app",
"apns_uuid" : "dffa5720-f2f1-416f-a31f-23fcfeed6778",
"app_name" : "AppName",
"configuration" : {
"CLIENT_REQUEST_TIME_VALIDATION_THRESHOLD" : "300000",
"RECOVERY_CODE_MIN_LENGTH" : "6",
"GEOFENCING_ACTIVATION_MODE" : "OFF",
"ATTESTATION_IOS_APP_ATTEST_TIMEOUT" : "20000",
"ATTESTATION_IOS_APP_ATTEST_ENVIRONMENT" : "PRODUCTION",
"RECOVERY_CODE_MAX_LENGTH" : "50",
"ALLOWED_AUTH_METHODS" : "\n DEVICE,\n DEVICE:PIN\n ",
"HWKEY_VALIDATION_STRATEGY" : "SUPPORTED",
"GEOFENCING_AUTHENTICATION_ALLOWED_CONTINENTS" : "",
"MAXIMUM_SESSION_EXPIRY" : "300000",
"SESSION_EXPIRY" : "300000",
"RECOVERY_ENABLED" : "false",
"RECOVERY_CODE_FORMAT" : "NUMERIC",
"MAX_PIN_CODE_LENGTH" : "6",
"TOKEN_TYPE" : "SAML2",
"AUTHORIZATION_TOKEN_TIMEOUT" : "300000",
"GEOFENCING_AUTHENTICATION_ALLOWED_COUNTRIES" : "",
"URL_SCHEME" : "encap",
"CLIENT_ONLY_ALLOWED" : "true",
"GEOFENCING_ACTIVATION_ALLOWED_CONTINENTS" : "",
"ATTESTATION_IOS_APP_ATTEST_MODE" : "OFF",
"ATTESTATION_ANDROID_SAFETYNET_MODE" : "OFF",
"APN_EXPIRY" : "86400000",
"APNS_TIME_SENSITIVE_INTERRUPTION_LEVEL_ENABLED" : "false",
"GEOFENCING_AUTHENTICATION_MODE" : "OFF",
"APN_CONFIG" : "PRODUCTION",
"CLIENT_REQUEST_TIME_VALIDATION_ENABLED" : "true",
"ACTIVATION_CODE_TYPE" : "NUMERIC",
"AMOUNT_FAILURES_ALLOWED" : "3",
"GEOFENCING_AUTHENTICATION_DENIED_COUNTRIES" : "",
"ACTIVATION_CODE_ALLOWED_GUESS_PROBABILITY" : "1000",
"ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE" : "OFF",
"APNS_NOTIFICATION_SOUND_ENABLED" : "false",
"CLIENT_DEBUG_DATA_ENABLED_OS_TYPES" : "",
"GEOFENCING_TIMEOUT" : "10000",
"PIN_CODE_LENGTH" : "4",
"GEOFENCING_ACTIVATION_ALLOWED_COUNTRIES" : "",
"ACTIVATION_CODE_LENGTH" : "6",
"PIN_CODE_TYPE" : "NUMERIC",
"GEOFENCING_ACTIVATION_DENIED_COUNTRIES" : "",
"NATIVE_PUSH_ENABLED" : "true",
"RECOVERY_CODE_AMOUNT_FAILURES_ALLOWED" : "3",
"FIREBASE_TIME_TO_LIVE" : "0",
"ATTESTATION_IOS_APP_ATTEST_APP_ID" : "",
"ALLOWED_AUTH_METHODS_FOR_AUTH_AND_ACTIVATE" : "\n DEVICE:PIN\n ",
"LOCK_SCOPE" : "AUTH_METHOD",
"ENABLED_RISK_DATA" : "ALL"
}
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: 539a6d0a-9973-4ca3-a57d-d9053b69a66a
Content-Type: application/json
Content-Length: 2283
{
"app_id" : "some-new-app",
"uuid" : "b3136c90-06dd-40c8-9527-89db5b01e2e6",
"apns_uuid" : "dffa5720-f2f1-416f-a31f-23fcfeed6778",
"configuration" : {
"CLIENT_REQUEST_TIME_VALIDATION_THRESHOLD" : "300000",
"RECOVERY_CODE_MIN_LENGTH" : "6",
"GEOFENCING_ACTIVATION_MODE" : "OFF",
"ATTESTATION_IOS_APP_ATTEST_TIMEOUT" : "20000",
"ATTESTATION_IOS_APP_ATTEST_ENVIRONMENT" : "PRODUCTION",
"RECOVERY_CODE_MAX_LENGTH" : "50",
"ALLOWED_AUTH_METHODS" : "\n DEVICE,\n DEVICE:PIN\n ",
"HWKEY_VALIDATION_STRATEGY" : "SUPPORTED",
"GEOFENCING_AUTHENTICATION_ALLOWED_CONTINENTS" : "",
"MAXIMUM_SESSION_EXPIRY" : "300000",
"SESSION_EXPIRY" : "300000",
"RECOVERY_ENABLED" : "false",
"RECOVERY_CODE_FORMAT" : "NUMERIC",
"MAX_PIN_CODE_LENGTH" : "6",
"TOKEN_TYPE" : "SAML2",
"AUTHORIZATION_TOKEN_TIMEOUT" : "300000",
"GEOFENCING_AUTHENTICATION_ALLOWED_COUNTRIES" : "",
"URL_SCHEME" : "encap",
"CLIENT_ONLY_ALLOWED" : "true",
"GEOFENCING_ACTIVATION_ALLOWED_CONTINENTS" : "",
"ATTESTATION_IOS_APP_ATTEST_MODE" : "OFF",
"ATTESTATION_ANDROID_SAFETYNET_MODE" : "OFF",
"APN_EXPIRY" : "86400000",
"APNS_TIME_SENSITIVE_INTERRUPTION_LEVEL_ENABLED" : "false",
"GEOFENCING_AUTHENTICATION_MODE" : "OFF",
"APN_CONFIG" : "PRODUCTION",
"CLIENT_REQUEST_TIME_VALIDATION_ENABLED" : "true",
"ACTIVATION_CODE_TYPE" : "NUMERIC",
"AMOUNT_FAILURES_ALLOWED" : "3",
"GEOFENCING_AUTHENTICATION_DENIED_COUNTRIES" : "",
"ACTIVATION_CODE_ALLOWED_GUESS_PROBABILITY" : "1000",
"ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE" : "OFF",
"APNS_NOTIFICATION_SOUND_ENABLED" : "false",
"CLIENT_DEBUG_DATA_ENABLED_OS_TYPES" : "",
"GEOFENCING_TIMEOUT" : "10000",
"PIN_CODE_LENGTH" : "4",
"GEOFENCING_ACTIVATION_ALLOWED_COUNTRIES" : "",
"ACTIVATION_CODE_LENGTH" : "6",
"PIN_CODE_TYPE" : "NUMERIC",
"GEOFENCING_ACTIVATION_DENIED_COUNTRIES" : "",
"NATIVE_PUSH_ENABLED" : "true",
"RECOVERY_CODE_AMOUNT_FAILURES_ALLOWED" : "3",
"FIREBASE_TIME_TO_LIVE" : "0",
"ATTESTATION_IOS_APP_ATTEST_APP_ID" : "",
"ALLOWED_AUTH_METHODS_FOR_AUTH_AND_ACTIVATE" : "\n DEVICE:PIN\n ",
"LOCK_SCOPE" : "AUTH_METHOD",
"ENABLED_RISK_DATA" : "ALL"
}
}4.2.4. Get application configuration
GET /api/admin/v1/appconfig/{uuid}
Returns the application configuration object with the uuid.
Example request
$ curl 'http://localhost:8080/api/admin/v1/appconfig/1b95893e-897c-445e-8627-d5df051be864' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GET \
-H 'Content-Type: application/json'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: ea01ee4d-d7c3-45aa-b7c7-c91fad47ade7
Content-Type: application/json
Content-Length: 2315
{
"app_id" : "encapApiTest",
"uuid" : "1b95893e-897c-445e-8627-d5df051be864",
"apns_uuid" : "136bffb4-140a-4b7a-917f-8e32e2c671fd",
"app_name" : "applicationName",
"configuration" : {
"ACTIVATION_CODE_ALLOWED_GUESS_PROBABILITY" : "1000",
"ACTIVATION_CODE_LENGTH" : "6",
"ACTIVATION_CODE_TYPE" : "NUMERIC",
"ALLOWED_AUTH_METHODS" : "\n DEVICE,\n DEVICE:PIN\n ",
"ALLOWED_AUTH_METHODS_FOR_AUTH_AND_ACTIVATE" : "\n DEVICE:PIN\n ",
"AMOUNT_FAILURES_ALLOWED" : "3",
"APNS_NOTIFICATION_SOUND_ENABLED" : "false",
"APNS_TIME_SENSITIVE_INTERRUPTION_LEVEL_ENABLED" : "false",
"APN_CONFIG" : "PRODUCTION",
"APN_EXPIRY" : "86400000",
"ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE" : "OFF",
"ATTESTATION_ANDROID_SAFETYNET_MODE" : "OFF",
"ATTESTATION_IOS_APP_ATTEST_APP_ID" : "",
"ATTESTATION_IOS_APP_ATTEST_ENVIRONMENT" : "PRODUCTION",
"ATTESTATION_IOS_APP_ATTEST_MODE" : "OFF",
"ATTESTATION_IOS_APP_ATTEST_TIMEOUT" : "20000",
"AUTHORIZATION_TOKEN_TIMEOUT" : "300000",
"CLIENT_DEBUG_DATA_ENABLED_OS_TYPES" : "",
"CLIENT_ONLY_ALLOWED" : "true",
"CLIENT_REQUEST_TIME_VALIDATION_ENABLED" : "true",
"CLIENT_REQUEST_TIME_VALIDATION_THRESHOLD" : "300000",
"ENABLED_RISK_DATA" : "",
"FIREBASE_TIME_TO_LIVE" : "0",
"GEOFENCING_ACTIVATION_ALLOWED_CONTINENTS" : "",
"GEOFENCING_ACTIVATION_ALLOWED_COUNTRIES" : "",
"GEOFENCING_ACTIVATION_DENIED_COUNTRIES" : "",
"GEOFENCING_ACTIVATION_MODE" : "OFF",
"GEOFENCING_AUTHENTICATION_ALLOWED_CONTINENTS" : "",
"GEOFENCING_AUTHENTICATION_ALLOWED_COUNTRIES" : "",
"GEOFENCING_AUTHENTICATION_DENIED_COUNTRIES" : "",
"GEOFENCING_AUTHENTICATION_MODE" : "OFF",
"GEOFENCING_TIMEOUT" : "10000",
"HWKEY_VALIDATION_STRATEGY" : "SUPPORTED",
"LOCK_SCOPE" : "AUTH_METHOD",
"MAXIMUM_SESSION_EXPIRY" : "300000",
"MAX_PIN_CODE_LENGTH" : "4",
"NATIVE_PUSH_ENABLED" : "false",
"PIN_CODE_LENGTH" : "4",
"PIN_CODE_TYPE" : "NUMERIC",
"RECOVERY_CODE_AMOUNT_FAILURES_ALLOWED" : "3",
"RECOVERY_CODE_FORMAT" : "NUMERIC",
"RECOVERY_CODE_MAX_LENGTH" : "50",
"RECOVERY_CODE_MIN_LENGTH" : "6",
"RECOVERY_ENABLED" : "false",
"SESSION_EXPIRY" : "300000",
"TOKEN_TYPE" : "SAML2",
"URL_SCHEME" : "encap"
}
}4.2.5. Get all application configurations
GET /api/admin/v1/appconfig?limit=10&offset=0
Returns a pagination object with a list of application configuration objects that belongs to your organization.
Example request
$ curl 'http://localhost:8080/api/admin/v1/appconfig?limit=3&offset=eb3fa978-faaf-4f2b-8cdb-e9df558d4882' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: e063aaf4-be28-498c-bf8d-e0585455ae2d
Content-Type: application/json
Content-Length: 7627
{
"previous" : "/admin/v1/appconfig?limit=3&offset=ab6cd8ca-6f61-492a-b81c-09d4ffebbfef",
"next" : "/admin/v1/appconfig?limit=3&offset=26e76b47-9a8d-42c6-9d08-112e9d9ec665",
"offset" : "eb3fa978-faaf-4f2b-8cdb-e9df558d4882",
"limit" : 3,
"items" : [ {
"app_id" : "Application-0",
"uuid" : "febf7fcb-a426-4ca4-8f93-2b406c86e4ec",
"apns_uuid" : "22587988-40eb-4c34-94c7-163780b9debc",
"app_name" : "Application Name 0",
"status" : "ENABLED",
"configuration" : {
"CLIENT_REQUEST_TIME_VALIDATION_THRESHOLD" : "300000",
"RECOVERY_CODE_MIN_LENGTH" : "6",
"GEOFENCING_ACTIVATION_MODE" : "OFF",
"ATTESTATION_IOS_APP_ATTEST_TIMEOUT" : "20000",
"ATTESTATION_IOS_APP_ATTEST_ENVIRONMENT" : "PRODUCTION",
"RECOVERY_CODE_MAX_LENGTH" : "50",
"ALLOWED_AUTH_METHODS" : "\n DEVICE,\n DEVICE:PIN\n ",
"HWKEY_VALIDATION_STRATEGY" : "SUPPORTED",
"GEOFENCING_AUTHENTICATION_ALLOWED_CONTINENTS" : "",
"MAXIMUM_SESSION_EXPIRY" : "300000",
"SESSION_EXPIRY" : "300000",
"RECOVERY_ENABLED" : "false",
"RECOVERY_CODE_FORMAT" : "NUMERIC",
"MAX_PIN_CODE_LENGTH" : "4",
"TOKEN_TYPE" : "SAML2",
"AUTHORIZATION_TOKEN_TIMEOUT" : "300000",
"GEOFENCING_AUTHENTICATION_ALLOWED_COUNTRIES" : "",
"URL_SCHEME" : "encap",
"CLIENT_ONLY_ALLOWED" : "true",
"GEOFENCING_ACTIVATION_ALLOWED_CONTINENTS" : "",
"ATTESTATION_IOS_APP_ATTEST_MODE" : "OFF",
"ATTESTATION_ANDROID_SAFETYNET_MODE" : "OFF",
"APN_EXPIRY" : "86400000",
"APNS_TIME_SENSITIVE_INTERRUPTION_LEVEL_ENABLED" : "false",
"GEOFENCING_AUTHENTICATION_MODE" : "OFF",
"APN_CONFIG" : "PRODUCTION",
"CLIENT_REQUEST_TIME_VALIDATION_ENABLED" : "true",
"ACTIVATION_CODE_TYPE" : "NUMERIC",
"AMOUNT_FAILURES_ALLOWED" : "3",
"GEOFENCING_AUTHENTICATION_DENIED_COUNTRIES" : "",
"ACTIVATION_CODE_ALLOWED_GUESS_PROBABILITY" : "1000",
"ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE" : "OFF",
"APNS_NOTIFICATION_SOUND_ENABLED" : "false",
"CLIENT_DEBUG_DATA_ENABLED_OS_TYPES" : "",
"GEOFENCING_TIMEOUT" : "10000",
"PIN_CODE_LENGTH" : "4",
"GEOFENCING_ACTIVATION_ALLOWED_COUNTRIES" : "",
"ACTIVATION_CODE_LENGTH" : "6",
"PIN_CODE_TYPE" : "NUMERIC",
"GEOFENCING_ACTIVATION_DENIED_COUNTRIES" : "",
"NATIVE_PUSH_ENABLED" : "false",
"RECOVERY_CODE_AMOUNT_FAILURES_ALLOWED" : "3",
"FIREBASE_TIME_TO_LIVE" : "0",
"ATTESTATION_IOS_APP_ATTEST_APP_ID" : "",
"ALLOWED_AUTH_METHODS_FOR_AUTH_AND_ACTIVATE" : "\n DEVICE:PIN\n ",
"LOCK_SCOPE" : "AUTH_METHOD",
"ENABLED_RISK_DATA" : ""
}
}, {
"app_id" : "Application-1",
"uuid" : "b696f5e1-c370-4694-a00e-0de91e59a56a",
"apns_uuid" : "220571bc-7fc2-463f-8250-3629160d52e0",
"app_name" : "Application Name 1",
"status" : "ENABLED",
"configuration" : {
"CLIENT_REQUEST_TIME_VALIDATION_THRESHOLD" : "300000",
"RECOVERY_CODE_MIN_LENGTH" : "6",
"GEOFENCING_ACTIVATION_MODE" : "OFF",
"ATTESTATION_IOS_APP_ATTEST_TIMEOUT" : "20000",
"ATTESTATION_IOS_APP_ATTEST_ENVIRONMENT" : "PRODUCTION",
"RECOVERY_CODE_MAX_LENGTH" : "50",
"ALLOWED_AUTH_METHODS" : "\n DEVICE,\n DEVICE:PIN\n ",
"HWKEY_VALIDATION_STRATEGY" : "SUPPORTED",
"GEOFENCING_AUTHENTICATION_ALLOWED_CONTINENTS" : "",
"MAXIMUM_SESSION_EXPIRY" : "300000",
"SESSION_EXPIRY" : "300000",
"RECOVERY_ENABLED" : "false",
"RECOVERY_CODE_FORMAT" : "NUMERIC",
"MAX_PIN_CODE_LENGTH" : "4",
"TOKEN_TYPE" : "SAML2",
"AUTHORIZATION_TOKEN_TIMEOUT" : "300000",
"GEOFENCING_AUTHENTICATION_ALLOWED_COUNTRIES" : "",
"URL_SCHEME" : "encap",
"CLIENT_ONLY_ALLOWED" : "true",
"GEOFENCING_ACTIVATION_ALLOWED_CONTINENTS" : "",
"ATTESTATION_IOS_APP_ATTEST_MODE" : "OFF",
"ATTESTATION_ANDROID_SAFETYNET_MODE" : "OFF",
"APN_EXPIRY" : "86400000",
"APNS_TIME_SENSITIVE_INTERRUPTION_LEVEL_ENABLED" : "false",
"GEOFENCING_AUTHENTICATION_MODE" : "OFF",
"APN_CONFIG" : "PRODUCTION",
"CLIENT_REQUEST_TIME_VALIDATION_ENABLED" : "true",
"ACTIVATION_CODE_TYPE" : "NUMERIC",
"AMOUNT_FAILURES_ALLOWED" : "3",
"GEOFENCING_AUTHENTICATION_DENIED_COUNTRIES" : "",
"ACTIVATION_CODE_ALLOWED_GUESS_PROBABILITY" : "1000",
"ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE" : "OFF",
"APNS_NOTIFICATION_SOUND_ENABLED" : "false",
"CLIENT_DEBUG_DATA_ENABLED_OS_TYPES" : "",
"GEOFENCING_TIMEOUT" : "10000",
"PIN_CODE_LENGTH" : "4",
"GEOFENCING_ACTIVATION_ALLOWED_COUNTRIES" : "",
"ACTIVATION_CODE_LENGTH" : "6",
"PIN_CODE_TYPE" : "NUMERIC",
"GEOFENCING_ACTIVATION_DENIED_COUNTRIES" : "",
"NATIVE_PUSH_ENABLED" : "false",
"RECOVERY_CODE_AMOUNT_FAILURES_ALLOWED" : "3",
"FIREBASE_TIME_TO_LIVE" : "0",
"ATTESTATION_IOS_APP_ATTEST_APP_ID" : "",
"ALLOWED_AUTH_METHODS_FOR_AUTH_AND_ACTIVATE" : "\n DEVICE:PIN\n ",
"LOCK_SCOPE" : "AUTH_METHOD",
"ENABLED_RISK_DATA" : ""
}
}, {
"app_id" : "Application-2",
"uuid" : "b93ce7b5-bbaa-4872-bcf1-2bd1bf439bc5",
"apns_uuid" : "f7248e6e-acc7-4408-bb60-4fd78540c2b9",
"app_name" : "Application Name 2",
"status" : "ENABLED",
"configuration" : {
"CLIENT_REQUEST_TIME_VALIDATION_THRESHOLD" : "300000",
"RECOVERY_CODE_MIN_LENGTH" : "6",
"GEOFENCING_ACTIVATION_MODE" : "OFF",
"ATTESTATION_IOS_APP_ATTEST_TIMEOUT" : "20000",
"ATTESTATION_IOS_APP_ATTEST_ENVIRONMENT" : "PRODUCTION",
"RECOVERY_CODE_MAX_LENGTH" : "50",
"ALLOWED_AUTH_METHODS" : "\n DEVICE,\n DEVICE:PIN\n ",
"HWKEY_VALIDATION_STRATEGY" : "SUPPORTED",
"GEOFENCING_AUTHENTICATION_ALLOWED_CONTINENTS" : "",
"MAXIMUM_SESSION_EXPIRY" : "300000",
"SESSION_EXPIRY" : "300000",
"RECOVERY_ENABLED" : "false",
"RECOVERY_CODE_FORMAT" : "NUMERIC",
"MAX_PIN_CODE_LENGTH" : "4",
"TOKEN_TYPE" : "SAML2",
"AUTHORIZATION_TOKEN_TIMEOUT" : "300000",
"GEOFENCING_AUTHENTICATION_ALLOWED_COUNTRIES" : "",
"URL_SCHEME" : "encap",
"CLIENT_ONLY_ALLOWED" : "true",
"GEOFENCING_ACTIVATION_ALLOWED_CONTINENTS" : "",
"ATTESTATION_IOS_APP_ATTEST_MODE" : "OFF",
"ATTESTATION_ANDROID_SAFETYNET_MODE" : "OFF",
"APN_EXPIRY" : "86400000",
"APNS_TIME_SENSITIVE_INTERRUPTION_LEVEL_ENABLED" : "false",
"GEOFENCING_AUTHENTICATION_MODE" : "OFF",
"APN_CONFIG" : "PRODUCTION",
"CLIENT_REQUEST_TIME_VALIDATION_ENABLED" : "true",
"ACTIVATION_CODE_TYPE" : "NUMERIC",
"AMOUNT_FAILURES_ALLOWED" : "3",
"GEOFENCING_AUTHENTICATION_DENIED_COUNTRIES" : "",
"ACTIVATION_CODE_ALLOWED_GUESS_PROBABILITY" : "1000",
"ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE" : "OFF",
"APNS_NOTIFICATION_SOUND_ENABLED" : "false",
"CLIENT_DEBUG_DATA_ENABLED_OS_TYPES" : "",
"GEOFENCING_TIMEOUT" : "10000",
"PIN_CODE_LENGTH" : "4",
"GEOFENCING_ACTIVATION_ALLOWED_COUNTRIES" : "",
"ACTIVATION_CODE_LENGTH" : "6",
"PIN_CODE_TYPE" : "NUMERIC",
"GEOFENCING_ACTIVATION_DENIED_COUNTRIES" : "",
"NATIVE_PUSH_ENABLED" : "false",
"RECOVERY_CODE_AMOUNT_FAILURES_ALLOWED" : "3",
"FIREBASE_TIME_TO_LIVE" : "0",
"ATTESTATION_IOS_APP_ATTEST_APP_ID" : "",
"ALLOWED_AUTH_METHODS_FOR_AUTH_AND_ACTIVATE" : "\n DEVICE:PIN\n ",
"LOCK_SCOPE" : "AUTH_METHOD",
"ENABLED_RISK_DATA" : ""
}
} ]
}4.2.6. Update application configuration
PATCH /api/admin/v1/appconfig/{uuid}
This patch API follows the RFC 7396 JSON Merge Patch standard.
The request body should only include fields that are to be updated.
To remove a field, set the value in the key value pair to null.
Absence of a key will cause no changes to that field value.
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
No |
The status of the application configuration. ENABLED, DISABLED. |
|
|
No |
The UUID of the APNs push certificate or token used. Required if NATIVE_PUSH_ENABLED is true. |
|
|
No |
The human readable name for the application configuration |
|
|
No |
The application configuration parameters. Parameters follow the JSON Merge Patch standard. Absent parameters will be unaffected. |
Returns
Returns an application configuration object if request is processed successfully. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/admin/v1/appconfig/cfff998a-1e5d-4d2c-b009-50b5b70b7949' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X PATCH \
-H 'Content-Type: application/merge-patch+json' \
-d '{
"apns_uuid" : "b3eca85d-0de4-4540-8e98-ce057cf75b35",
"app_name" : "New Application Name",
"status" : "DISABLED",
"configuration" : {
"ATTESTATION_IOS_APP_ATTEST_TIMEOUT" : null,
"CLIENT_ONLY_ALLOWED" : "false"
}
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: 7a7a4d50-a477-4345-977d-c62bdf16adc7
Content-Type: application/json
Content-Length: 2294
{
"app_id" : "some-new-app",
"uuid" : "cfff998a-1e5d-4d2c-b009-50b5b70b7949",
"apns_uuid" : "b3eca85d-0de4-4540-8e98-ce057cf75b35",
"app_name" : "New Application Name",
"status" : "DISABLED",
"configuration" : {
"CLIENT_REQUEST_TIME_VALIDATION_THRESHOLD" : "300000",
"RECOVERY_CODE_MIN_LENGTH" : "6",
"GEOFENCING_ACTIVATION_MODE" : "OFF",
"ATTESTATION_IOS_APP_ATTEST_ENVIRONMENT" : "PRODUCTION",
"RECOVERY_CODE_MAX_LENGTH" : "50",
"ALLOWED_AUTH_METHODS" : "\n DEVICE,\n DEVICE:PIN\n ",
"HWKEY_VALIDATION_STRATEGY" : "SUPPORTED",
"GEOFENCING_AUTHENTICATION_ALLOWED_CONTINENTS" : "",
"MAXIMUM_SESSION_EXPIRY" : "300000",
"SESSION_EXPIRY" : "300000",
"RECOVERY_ENABLED" : "false",
"RECOVERY_CODE_FORMAT" : "NUMERIC",
"MAX_PIN_CODE_LENGTH" : "4",
"TOKEN_TYPE" : "SAML2",
"AUTHORIZATION_TOKEN_TIMEOUT" : "300000",
"GEOFENCING_AUTHENTICATION_ALLOWED_COUNTRIES" : "",
"URL_SCHEME" : "encap",
"CLIENT_ONLY_ALLOWED" : "false",
"GEOFENCING_ACTIVATION_ALLOWED_CONTINENTS" : "",
"ATTESTATION_IOS_APP_ATTEST_MODE" : "OFF",
"ATTESTATION_ANDROID_SAFETYNET_MODE" : "OFF",
"APN_EXPIRY" : "86400000",
"APNS_TIME_SENSITIVE_INTERRUPTION_LEVEL_ENABLED" : "false",
"GEOFENCING_AUTHENTICATION_MODE" : "OFF",
"APN_CONFIG" : "PRODUCTION",
"CLIENT_REQUEST_TIME_VALIDATION_ENABLED" : "true",
"ACTIVATION_CODE_TYPE" : "NUMERIC",
"AMOUNT_FAILURES_ALLOWED" : "3",
"GEOFENCING_AUTHENTICATION_DENIED_COUNTRIES" : "",
"ACTIVATION_CODE_ALLOWED_GUESS_PROBABILITY" : "1000",
"ATTESTATION_ANDROID_PLAY_INTEGRITY_MODE" : "OFF",
"APNS_NOTIFICATION_SOUND_ENABLED" : "false",
"CLIENT_DEBUG_DATA_ENABLED_OS_TYPES" : "",
"GEOFENCING_TIMEOUT" : "10000",
"PIN_CODE_LENGTH" : "4",
"GEOFENCING_ACTIVATION_ALLOWED_COUNTRIES" : "",
"ACTIVATION_CODE_LENGTH" : "6",
"PIN_CODE_TYPE" : "NUMERIC",
"GEOFENCING_ACTIVATION_DENIED_COUNTRIES" : "",
"NATIVE_PUSH_ENABLED" : "false",
"RECOVERY_CODE_AMOUNT_FAILURES_ALLOWED" : "3",
"FIREBASE_TIME_TO_LIVE" : "0",
"ATTESTATION_IOS_APP_ATTEST_APP_ID" : "",
"ALLOWED_AUTH_METHODS_FOR_AUTH_AND_ACTIVATE" : "\n DEVICE:PIN\n ",
"LOCK_SCOPE" : "AUTH_METHOD",
"ENABLED_RISK_DATA" : ""
}
}4.2.7. Delete application configuration
DELETE /api/admin/v1/appconfig/{uuid}
Removes an application configuration with the uuid.
Example request
$ curl 'http://localhost:8080/api/admin/v1/appconfig/aaa6a882-0f5b-470c-8b3b-1254a83ffd1e' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETE \
-H 'Content-Type: application/json'Example response
HTTP/1.1 202 Accepted
X-Correlation-UUID: 072e4b07-6b36-4b8e-9da8-5a43be13c8f94.3. APNs Certificate
An API to create and retrieve APNs Certificates. Once a certificate is associated with an application configuration, that application will then use the APNs Certificate to send push notifications to Apple devices. Encap supports APNs tokens, for details on how configure an APNs token please see the Encap Administration Manual.
4.3.1. The APNs object
| Field | Type | Description |
|---|---|---|
|
|
The UUID for the APNS certificate |
|
|
The name of the APNS certificate |
|
|
The SHA1 hash of the APNS certificate |
|
|
The SHA256 hash of the APNS certificate |
|
|
The description of the APNS certificate |
|
|
The start date of the certificate validity period |
|
|
The end date of the certificate validity period |
|
|
The subject distinguished name from the certificate |
|
|
The issuer distinguished name from the certificate |
|
|
The name/id of the creator of the APNS certificate |
|
|
The date for when the APNS certificate was created. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
4.3.2. Create APNs Certificate
POST /api/admin/v1/apns
Creates a new APNs Certificate with the provided values
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
The name of the APNS certificate |
|
|
No |
The description of the APNS certificate |
|
|
Yes |
The Base64 encoded string of the APNS certificate bytes |
|
|
Yes |
The password associated with the APNS certificate |
Returns
Returns an apns certificate object if the request was processed successfully, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/admin/v1/apns' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"name" : "test-cert-name",
"description" : "test-cert-description",
"apns_certificate_b64" : "somelongb64encodedstring",
"password" : "test-cert-password"
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: a6b41da0-ecf8-4046-9c84-e9a0a7ce94a3
Content-Type: application/json
Content-Length: 739
{
"id" : "027a091f-af0c-4b98-8c23-1b7d3ec08874",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:55.489UTC",
"sha1_fingerprint" : "d0:5b:e1:40:6e:78:5d:10:cf:a8:67:c5:5a:02:5b:7f:de:7d:93:d2",
"sha256_fingerprint" : "c3:64:fb:f9:a8:46:04:5c:ed:ef:bc:1c:78:00:cb:b7:6d:67:64:50:16:cd:3e:5e:69:04:30:5c:59:ff:02:4a",
"valid_from" : "2025-01-31T12:26:56.000UTC",
"valid_until" : "2026-03-02T12:26:55.000UTC",
"subject" : "C=NO,O=Signicat AS,OU=Y2Y8VXX8PM,CN=Apple Push Services: com.signicat.encap.TestApp,UID=com.signicat.encap.TestApp",
"issuer" : "C=US,O=Apple Inc.,OU=G4,CN=Apple Worldwide Developer Relations Certification Authority"
}4.3.3. Get APNs Certificate details
GET /api/admin/v1/apns/{apnsId}
Get meta data for the APNs Certificate
Returns
Returns a apns certificate object if a valid identifier was provided, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/admin/v1/apns/027a091f-af0c-4b98-8c23-1b7d3ec08874' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 1bff0723-1949-4573-ba49-2e5038c528eb
Content-Type: application/json
Content-Length: 739
{
"id" : "027a091f-af0c-4b98-8c23-1b7d3ec08874",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:56.241UTC",
"sha1_fingerprint" : "d0:5b:e1:40:6e:78:5d:10:cf:a8:67:c5:5a:02:5b:7f:de:7d:93:d2",
"sha256_fingerprint" : "c3:64:fb:f9:a8:46:04:5c:ed:ef:bc:1c:78:00:cb:b7:6d:67:64:50:16:cd:3e:5e:69:04:30:5c:59:ff:02:4a",
"valid_from" : "2025-01-31T12:26:56.000UTC",
"valid_until" : "2026-03-02T12:26:55.000UTC",
"subject" : "C=NO,O=Signicat AS,OU=Y2Y8VXX8PM,CN=Apple Push Services: com.signicat.encap.TestApp,UID=com.signicat.encap.TestApp",
"issuer" : "C=US,O=Apple Inc.,OU=G4,CN=Apple Worldwide Developer Relations Certification Authority"
}4.3.4. Get all APNs Certificates
GET /api/admin/v1/apns
Returns a pagination object with a list of apns certificate objects that belongs to your organization.
Example request
$ curl 'http://localhost:8080/api/admin/v1/apns?limit=3&offset=1667c767-9361-44f4-8965-bebba413162e' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 96f23b91-0dcf-4fec-9ee5-92b1f8410a57
Content-Type: application/json
Content-Length: 2547
{
"previous" : "/admin/v1/apns?limit=3&offset=54994667-a795-4273-820c-59cc1a303295",
"next" : "/admin/v1/apns?limit=3&offset=73a126a7-58a7-4ebd-b94e-df69cb371335",
"offset" : "1667c767-9361-44f4-8965-bebba413162e",
"limit" : 3,
"items" : [ {
"id" : "250f0cc1-c279-41d0-a985-2c57525836eb",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:55.690UTC",
"sha1_fingerprint" : "d0:5b:e1:40:6e:78:5d:10:cf:a8:67:c5:5a:02:5b:7f:de:7d:93:d2",
"sha256_fingerprint" : "c3:64:fb:f9:a8:46:04:5c:ed:ef:bc:1c:78:00:cb:b7:6d:67:64:50:16:cd:3e:5e:69:04:30:5c:59:ff:02:4a",
"valid_from" : "2025-01-31T12:26:56.000UTC",
"valid_until" : "2026-03-02T12:26:55.000UTC",
"subject" : "C=NO,O=Signicat AS,OU=Y2Y8VXX8PM,CN=Apple Push Services: com.signicat.encap.TestApp,UID=com.signicat.encap.TestApp",
"issuer" : "C=US,O=Apple Inc.,OU=G4,CN=Apple Worldwide Developer Relations Certification Authority"
}, {
"id" : "b1782c46-2097-4e2c-ae50-e1c91afce08d",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:55.788UTC",
"sha1_fingerprint" : "d0:5b:e1:40:6e:78:5d:10:cf:a8:67:c5:5a:02:5b:7f:de:7d:93:d2",
"sha256_fingerprint" : "c3:64:fb:f9:a8:46:04:5c:ed:ef:bc:1c:78:00:cb:b7:6d:67:64:50:16:cd:3e:5e:69:04:30:5c:59:ff:02:4a",
"valid_from" : "2025-01-31T12:26:56.000UTC",
"valid_until" : "2026-03-02T12:26:55.000UTC",
"subject" : "C=NO,O=Signicat AS,OU=Y2Y8VXX8PM,CN=Apple Push Services: com.signicat.encap.TestApp,UID=com.signicat.encap.TestApp",
"issuer" : "C=US,O=Apple Inc.,OU=G4,CN=Apple Worldwide Developer Relations Certification Authority"
}, {
"id" : "c8ee18dc-b8b8-4e7c-b5b7-ecf33671bb51",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:55.906UTC",
"sha1_fingerprint" : "d0:5b:e1:40:6e:78:5d:10:cf:a8:67:c5:5a:02:5b:7f:de:7d:93:d2",
"sha256_fingerprint" : "c3:64:fb:f9:a8:46:04:5c:ed:ef:bc:1c:78:00:cb:b7:6d:67:64:50:16:cd:3e:5e:69:04:30:5c:59:ff:02:4a",
"valid_from" : "2025-01-31T12:26:56.000UTC",
"valid_until" : "2026-03-02T12:26:55.000UTC",
"subject" : "C=NO,O=Signicat AS,OU=Y2Y8VXX8PM,CN=Apple Push Services: com.signicat.encap.TestApp,UID=com.signicat.encap.TestApp",
"issuer" : "C=US,O=Apple Inc.,OU=G4,CN=Apple Worldwide Developer Relations Certification Authority"
} ]
}4.3.5. Delete APNs Certificate
DELETE /api/admin/v1/apns/{apnsId}
Deletes the APNs certificate with the apnsId
Example request
$ curl 'http://localhost:8080/api/admin/v1/apns/e47add48-44e1-42ad-a535-d275d383d3e4' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: bdf6bf2c-f7ce-4777-b998-b200f248db494.4. APNs Provider Token
An API to add and retrieve APNs provider tokens.
4.4.1. The APNs provider token object
| Field | Type | Description |
|---|---|---|
|
|
The UUID for the APNs token |
|
|
The name of the APNs token |
|
|
The SHA1 hash of the APNs token |
|
|
The SHA256 hash of the APNs token |
|
|
The description of the APNs token |
|
|
Key ID of the APNs token |
|
|
Team ID of Apple Developer Account |
|
|
The name/id of the creator of the APNs token |
|
|
The date for when the APNs token was created. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
4.4.2. Add APNs provider token
POST /api/admin/v1/apnstokens
Adds a new APNs provider token with the provided values (from the Apple Developer Portal).
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
The name of the APNs token |
|
|
No |
The description of the APNs token |
|
|
Yes |
The Base64 encoded string of APNs token private key |
|
|
Yes |
Key ID of the APNs token |
|
|
Yes |
Team ID of Apple Developer Account |
Returns
Returns an APNs provider token object if the request was processed successfully, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/admin/v1/apnstokens' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"name" : "test-token-name",
"description" : "test-token-description",
"private_key_b64" : "privateKeyString",
"key_id" : "key-id",
"team_id" : "team-id"
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: 9552d985-fffb-425e-99af-7dfb792ce95d
Content-Type: application/json
Content-Length: 467
{
"id" : "de693fbe-eee4-4ecc-8cf6-c4f91514ecd6",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:55.175UTC",
"sha1_fingerprint" : "aa:6b:bb:f2:e3:5e:8f:91:5b:db:11:0a:27:45:0d:59:61:73:3d:6e",
"sha256_fingerprint" : "29:31:57:72:39:ec:78:84:ad:30:68:1a:e3:dc:5a:19:a5:4b:0c:f5:05:c7:48:56:14:59:28:a0:67:97:18:99",
"key_id" : "test-key-id",
"team_id" : "test-team-id"
}4.4.3. Get APNs provider token details
GET /api/admin/v1/apnstokens/{apnsTokenId}
Get metadata for an APNs provider token
Returns
Returns a APNs provider token object if a valid identifier was provided, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/admin/v1/apnstokens/de693fbe-eee4-4ecc-8cf6-c4f91514ecd6' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 9fec9fbc-7bd1-4dea-8e8a-66adc4092798
Content-Type: application/json
Content-Length: 467
{
"id" : "de693fbe-eee4-4ecc-8cf6-c4f91514ecd6",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:55.572UTC",
"sha1_fingerprint" : "aa:6b:bb:f2:e3:5e:8f:91:5b:db:11:0a:27:45:0d:59:61:73:3d:6e",
"sha256_fingerprint" : "29:31:57:72:39:ec:78:84:ad:30:68:1a:e3:dc:5a:19:a5:4b:0c:f5:05:c7:48:56:14:59:28:a0:67:97:18:99",
"key_id" : "test-key-id",
"team_id" : "test-team-id"
}4.4.4. Get all APNs provider tokens
GET /api/admin/v1/apnstokens
Returns a pagination object with a list of APNs provider token objects that belongs to your organization.
Example request
$ curl 'http://localhost:8080/api/admin/v1/apnstokens?limit=3&offset=be42c151-2129-45d8-a57b-c1ace78e4b8d' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: ab9a869f-b686-457d-b17f-f6125a5e53e2
Content-Type: application/json
Content-Length: 1731
{
"previous" : "/admin/v1/apnstokens?limit=3&offset=36cc015d-b66f-4245-b27c-469743cf253e",
"next" : "/admin/v1/apnstokens?limit=3&offset=8f559918-a703-44f9-9696-7d46134b67dd",
"offset" : "be42c151-2129-45d8-a57b-c1ace78e4b8d",
"limit" : 3,
"items" : [ {
"id" : "895a6546-731c-4f93-9634-89ba2add4ab1",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:55.050UTC",
"sha1_fingerprint" : "aa:6b:bb:f2:e3:5e:8f:91:5b:db:11:0a:27:45:0d:59:61:73:3d:6e",
"sha256_fingerprint" : "29:31:57:72:39:ec:78:84:ad:30:68:1a:e3:dc:5a:19:a5:4b:0c:f5:05:c7:48:56:14:59:28:a0:67:97:18:99",
"key_id" : "test-key-id",
"team_id" : "test-team-id"
}, {
"id" : "e3d40272-aa25-43e1-ab23-92904096bc65",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:55.050UTC",
"sha1_fingerprint" : "aa:6b:bb:f2:e3:5e:8f:91:5b:db:11:0a:27:45:0d:59:61:73:3d:6e",
"sha256_fingerprint" : "29:31:57:72:39:ec:78:84:ad:30:68:1a:e3:dc:5a:19:a5:4b:0c:f5:05:c7:48:56:14:59:28:a0:67:97:18:99",
"key_id" : "test-key-id",
"team_id" : "test-team-id"
}, {
"id" : "544905e8-fd4e-46a6-839c-db1671dc89c1",
"name" : "test-cert-name",
"description" : "test-cert-description",
"created_by" : "someuser",
"created_on" : "2025-10-28T13:49:55.050UTC",
"sha1_fingerprint" : "aa:6b:bb:f2:e3:5e:8f:91:5b:db:11:0a:27:45:0d:59:61:73:3d:6e",
"sha256_fingerprint" : "29:31:57:72:39:ec:78:84:ad:30:68:1a:e3:dc:5a:19:a5:4b:0c:f5:05:c7:48:56:14:59:28:a0:67:97:18:99",
"key_id" : "test-key-id",
"team_id" : "test-team-id"
} ]
}4.4.5. Delete APNs provider token
DELETE /api/admin/v1/apnstokens/{apnsTokenId}
Deletes the APNs provider token with the apnsTokenId
Example request
$ curl 'http://localhost:8080/api/admin/v1/apnstokens/47690a93-f367-4a6f-b54b-d252a492d4f5' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: 0bddac5e-a762-4bb8-8c58-c7f1ddf6ec624.5. API Key
An API to manage API keys. API keys are used to authenticate on all Encap REST APIs.
4.5.1. The API key object
| Field | Type | Description |
|---|---|---|
|
|
The API key ID, UUID, for the key. |
|
|
The API key secret. The secret is only part of the response when a API key is created, it is not returned when you fetch an API key |
|
|
The description for the API key |
|
|
The name/id of the creator of the API key |
|
|
The date for when the API key was created. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
4.5.2. Create API Key
POST /api/admin/v1/api-keys
Create a new API key
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
No |
The description for the API key |
Returns
Example request
$ curl 'http://localhost:8080/api/admin/v1/api-keys' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"description" : "Key for client A"
}'Example response
HTTP/1.1 201 Created
X-Correlation-UUID: edeab8a3-ca46-4ff5-a64f-d3955cf64038
Location: /admin/v1/api-keys/41ba3c42-e8f7-4774-923d-1dc2c0ac88d9
Content-Type: application/json
Content-Length: 250
{
"api_key_id" : "41ba3c42-e8f7-4774-923d-1dc2c0ac88d9",
"created_on" : "2025-10-28T13:49:53.156UTC",
"created_by" : "5a1b356e-5c7c-40af-98d1-a7ac20787bfa",
"description" : "Key for client A",
"api_key_secret" : "7guXojhkDaSub+NM9+n/iQ=="
}4.5.3. Get API key details
GET /api/admin/v1/api-keys/{api_key_id}
Get details for an API key.
Returns
Example request
$ curl 'http://localhost:8080/api/admin/v1/api-keys/41ba3c42-e8f7-4774-923d-1dc2c0ac88d9' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 31830610-3a80-4b64-b668-43599db57cba
Content-Type: application/json
Content-Length: 201
{
"api_key_id" : "41ba3c42-e8f7-4774-923d-1dc2c0ac88d9",
"created_on" : "2025-10-28T13:49:53.955UTC",
"created_by" : "5a1b356e-5c7c-40af-98d1-a7ac20787bfa",
"description" : "Key for client A"
}4.5.4. Get all API keys
GET /api/admin/v1/api-keys
Returns a pagination object with a list of API key objects that belongs your organization.
Example request
$ curl 'http://localhost:8080/api/admin/v1/api-keys?limit=3&offset=5be8b058-be4c-414c-b543-5faffdd33ed9' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 58283b51-d95f-4977-9d12-2a9803d97aec
Content-Type: application/json
Content-Length: 899
{
"previous" : "/admin/v1/api-keys?limit=3&offset=30391fb9-809c-443b-864d-ff3b69ba987d",
"next" : "/admin/v1/api-keys?limit=3&offset=7fcfc034-6ad7-4478-9e61-53c5844cef4c",
"offset" : "5be8b058-be4c-414c-b543-5faffdd33ed9",
"limit" : 3,
"items" : [ {
"api_key_id" : "dcebf34a-f293-408b-b0be-6a24c8281a44",
"created_on" : "2025-10-28T13:49:54.094UTC",
"created_by" : "5a1b356e-5c7c-40af-98d1-a7ac20787bfa",
"description" : "Key for client A"
}, {
"api_key_id" : "732f2162-88ce-4451-9dd0-97c6de18108e",
"created_on" : "2025-10-28T13:49:54.094UTC",
"created_by" : "5a1b356e-5c7c-40af-98d1-a7ac20787bfa",
"description" : "Key for client A"
}, {
"api_key_id" : "caad0d3a-d6d7-4c51-b2f9-13254e8319ec",
"created_on" : "2025-10-28T13:49:54.094UTC",
"created_by" : "5a1b356e-5c7c-40af-98d1-a7ac20787bfa",
"description" : "Key for client A"
} ]
}4.5.5. Delete API key
DELETE /api/admin/v1/api-keys/{api_key_id}
Deletes the API key with the specified id
Example request
$ curl 'http://localhost:8080/api/admin/v1/api-keys/41ba3c42-e8f7-4774-923d-1dc2c0ac88d9' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: 9c79ea81-5fc0-4cd6-8448-d6aa0f6817f14.6. End-to-End Key
End-to-End keys are used by Encap to create an additional encryption layer between the Encap Server and the SDK. This API is used to create and manage the End-to-End encryption keys used in this layer. Each organisation needs at least one End-to-End Key, but preferably you should have one key per application.
4.6.1. The End-to-End Key Object
| Field | Type | Description |
|---|---|---|
|
|
The UUID for the End-To-End key |
|
|
Name for the End-To-End key |
|
|
Description for the End-To-End key |
|
|
The name/id of the creator of the End-To-End key |
|
|
The date for when the End-To-End key was created. Returned in pattern yyyy-MM-dd’T’HH:mm:ss.SSS’UTC' |
|
|
The SHA256 hash of the End-To-End key certificate |
|
|
Base64 encoded End-To-End key certificate |
|
|
The UUID for the organization that owns this End-To-End key |
|
|
Status of the End-To-End key. Possible values are ENABLED and DISABLED |
4.6.2. Create End-to-End Key
POST /api/admin/v1/e2e-keys
Create a new End-to-End Key. A new End-to-End key pair is generated by the server and the public key is sent back in the response.
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
The name of the End-To-End key |
|
|
No |
Description for the End-To-End key |
Returns
Returns an End-to-End Key object if the request was processed successfully, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/admin/v1/e2e-keys' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"name" : "test-e2e-key-name",
"description" : "test-e2e-key-description"
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: 9ed47528-f39c-46f5-ad7a-a9d3a67c947e
Content-Type: application/json
Content-Length: 551
{
"id" : "9999e032-94cf-4ea4-96ac-ab665018d10a",
"name" : "test-e2e-cert-name",
"description" : "test-e2e-cert-description",
"created_by" : "someuser",
"created_on" : "2022-11-30T18:35:24.000UTC",
"sha256_fingerprint" : "71:04:a9:dc:e4:3c:23:fe:d8:d3:8f:79:f0:d7:1a:2e:35:7d:c6:de:6d:fd:19:9e:07:74:23:35:82:83:37:22",
"public_key" : "MFIwEAYHKoZIzj0CAQYFK4EEABoDPgAEAfdEY0BYY8yINZaHED77apY3/nZK3HZSnkUOrqUVAUcHe+RGt/iitJy8CGQmMjPA/gql5mREyiAPAPg2",
"organization_id" : "ff5f2648-bcbb-4c7f-8f92-00aa142b3cc4",
"status" : "DISABLED"
}4.6.3. Get End-to-End Key details
GET /api/admin/v1/e2e-keys/{e2eKeyId}
Get details for an End-to-End Key.
Returns
Returns a End-to-End Key object if a valid identifier was provided, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/admin/v1/e2e-keys/9999e032-94cf-4ea4-96ac-ab665018d10a' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 9fe33d78-4f0d-4a0c-91ef-d3c86e3e1e51
Content-Type: application/json
Content-Length: 551
{
"id" : "9999e032-94cf-4ea4-96ac-ab665018d10a",
"name" : "test-e2e-cert-name",
"description" : "test-e2e-cert-description",
"created_by" : "someuser",
"created_on" : "2022-11-30T18:35:24.000UTC",
"sha256_fingerprint" : "71:04:a9:dc:e4:3c:23:fe:d8:d3:8f:79:f0:d7:1a:2e:35:7d:c6:de:6d:fd:19:9e:07:74:23:35:82:83:37:22",
"public_key" : "MFIwEAYHKoZIzj0CAQYFK4EEABoDPgAEAfdEY0BYY8yINZaHED77apY3/nZK3HZSnkUOrqUVAUcHe+RGt/iitJy8CGQmMjPA/gql5mREyiAPAPg2",
"organization_id" : "2fe7cf9e-bee9-4c64-80ed-8b85b7cc0ccf",
"status" : "DISABLED"
}4.6.4. Get all End-to-End Keys
GET /api/admin/v1/e2e-keys
Returns a pagination object with a list of End-to-End Key objects that belongs your organization.
Example request
$ curl 'http://localhost:8080/api/admin/v1/e2e-keys?limit=3&offset=80c66d88-7bae-478b-9802-a2a6fd2ad76e' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 216d8e21-8b90-4ebc-9054-5b4a040018f7
Content-Type: application/json
Content-Length: 1979
{
"previous" : "/admin/v1/e2e-keys?limit=3&offset=40cd6dad-f6be-4be9-9387-bc8c3775631c",
"next" : "/admin/v1/e2e-keys?limit=3&offset=bf661022-5467-4457-bc6d-ed40f8141ac7",
"offset" : "80c66d88-7bae-478b-9802-a2a6fd2ad76e",
"limit" : 3,
"items" : [ {
"id" : "08d4e217-e1dd-479b-8217-07e42054e384",
"name" : "test-e2e-cert-name",
"description" : "test-e2e-cert-description",
"created_by" : "someuser",
"created_on" : "2022-11-30T18:35:24.000UTC",
"sha256_fingerprint" : "71:04:a9:dc:e4:3c:23:fe:d8:d3:8f:79:f0:d7:1a:2e:35:7d:c6:de:6d:fd:19:9e:07:74:23:35:82:83:37:22",
"public_key" : "MFIwEAYHKoZIzj0CAQYFK4EEABoDPgAEAfdEY0BYY8yINZaHED77apY3/nZK3HZSnkUOrqUVAUcHe+RGt/iitJy8CGQmMjPA/gql5mREyiAPAPg2",
"organization_id" : "f9cd3840-36f6-40b1-a296-9bd8e131570d",
"status" : "DISABLED"
}, {
"id" : "82477330-651b-472e-939c-08bb2fe66936",
"name" : "test-e2e-cert-name",
"description" : "test-e2e-cert-description",
"created_by" : "someuser",
"created_on" : "2022-11-30T18:35:24.000UTC",
"sha256_fingerprint" : "71:04:a9:dc:e4:3c:23:fe:d8:d3:8f:79:f0:d7:1a:2e:35:7d:c6:de:6d:fd:19:9e:07:74:23:35:82:83:37:22",
"public_key" : "MFIwEAYHKoZIzj0CAQYFK4EEABoDPgAEAfdEY0BYY8yINZaHED77apY3/nZK3HZSnkUOrqUVAUcHe+RGt/iitJy8CGQmMjPA/gql5mREyiAPAPg2",
"organization_id" : "da161c22-9347-4a32-b21d-afd59f0d7862",
"status" : "DISABLED"
}, {
"id" : "5430dc18-f2f6-46a9-bccb-4562398a3e93",
"name" : "test-e2e-cert-name",
"description" : "test-e2e-cert-description",
"created_by" : "someuser",
"created_on" : "2022-11-30T18:35:24.000UTC",
"sha256_fingerprint" : "71:04:a9:dc:e4:3c:23:fe:d8:d3:8f:79:f0:d7:1a:2e:35:7d:c6:de:6d:fd:19:9e:07:74:23:35:82:83:37:22",
"public_key" : "MFIwEAYHKoZIzj0CAQYFK4EEABoDPgAEAfdEY0BYY8yINZaHED77apY3/nZK3HZSnkUOrqUVAUcHe+RGt/iitJy8CGQmMjPA/gql5mREyiAPAPg2",
"organization_id" : "7c2decf6-b035-415e-8f33-dec24599778e",
"status" : "DISABLED"
} ]
}4.6.5. Update status of End-to-End Key
PUT /api/admin/v1/e2e-keys/{e2eKeyId}/status
Changing the status of the key. Changing status to DISABLED means that it will no longer be usable for client requests.
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
Status to set for the End-To-End key. Possible values are ENABLED and DISABLED |
Example request
$ curl 'http://localhost:8080/api/admin/v1/e2e-keys/9999e032-94cf-4ea4-96ac-ab665018d10a/status' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X PUT \
-H 'Content-Type: application/json' \
-d '{
"status" : "DISABLED"
}'Example response
HTTP/1.1 200 OK
X-Correlation-UUID: c2a19c0b-1cdc-48b2-be62-88f0b6b0a664
Content-Type: application/json
Content-Length: 27
{
"status" : "DISABLED"
}4.6.6. Delete End-to-End Key
DELETE /api/admin/v1/e2e-keys/{e2eKeyId}
Deletes the End-to-End Key with the specified id. You can only delete unused keys (having status set to DISABLED).
Example request
$ curl 'http://localhost:8080/api/admin/v1/e2e-keys/9999e032-94cf-4ea4-96ac-ab665018d10a' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X DELETEExample response
HTTP/1.1 204 No Content
X-Correlation-UUID: 73e97af0-6f8b-40f6-a466-d1fb255062d85. Statistics API
5.1. Encap client versions
An API for extracting statistics about the Encap client version for the devices registered in Encap. The statistics result will provide information on the amount of registrations that has been active within a given time interval, grouped by the Encap version of the client.
5.1.1. Usage
The version statistics extraction is a two-step progress because the actual data-extraction might take some time given a large dataset.
The first call, a POST request, will creates a new asynchrounous job for extracting the version statistics, the request returns an UUID for the version statistics result. This UUID is used in the second step. The second call, a GET request, gets the result of version statistics. If you perform a GET request before the extraction job has finished, the response will have the status IN_PROGRESS.
We also provided a cache functionality for the statistic extraction. If you make a new POST request for the same application configuration and the same time interval as a previous request, that has finished within the cache time period, then the server will not create a new job for extracting the same data. But instead return with the status READY and the UUID of the previous version statistics as a reference. To get the complete response perform a GET request for that UUID. If the previous version extraction has not yet finished, then the server will not start a new extraction job regardless of the cache time, but instead return with the status IN_PROGRESS and the UUID of the previous version statistics as a reference. To get the complete response perform a GET request for that UUID.
The cache time has a default value of one hour. You can change the cache time by providing the cluster-property admin.statistics.cachetime.
This value is an integer of seconds.
5.1.2. The encap client versions object
| Field | Type | Description |
|---|---|---|
|
|
The id of the statistics record |
|
|
Status of the statistics record. May be IN_PROGRESS, READY or FAILED |
|
|
UUID of the app config the statistics are generated for |
|
|
Registrations used after the number of days from this field will be included in the statistic |
|
|
The time the record was first created |
|
|
Number of devices used in the last amount of days, dictated by last_used, this is split by version |
| Field | Type | Description |
|---|---|---|
|
|
Encap client version |
|
|
Number of devices on this version |
5.1.3. Request statistics
POST /api/statistics/v1/encap-client-versions
Arguments
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
UUID of the app config the statistics are generated for |
|
|
Yes |
Registrations used after the number of days from this field will be included in the statistic |
Example request body
{
"app_config_uuid" : "5819c469-ec0d-4757-bf9a-5498e609076d",
"last_used" : 365
}Returns
Returns an encap client versions object if the request statistics is successfully initiated. Returns an error object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/statistics/v1/encap-client-versions' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X POST \
-H 'Content-Type: application/json' \
-d '{
"app_config_uuid" : "5819c469-ec0d-4757-bf9a-5498e609076d",
"last_used" : 365
}'Example response:
HTTP/1.1 202 Accepted
X-Correlation-UUID: 3c788f34-9a4a-43c3-ae27-661bf36f48a5
Content-Type: application/json
Content-Length: 243
{
"uuid" : "f68a6751-a800-4138-81a1-54efdc7af297",
"status" : "IN_PROGRESS",
"app_config_uuid" : "5819c469-ec0d-4757-bf9a-5498e609076d",
"last_used" : 365,
"generated_on" : "2025-10-28T13:49:57.679UTC",
"version_statistics" : [ ]
}5.1.4. Get statistics record
GET /api/statistics/v1/encap-client-versions/{uuid}
Returns
Returns an encap client versions object if a valid identifier was provided, and returns an error otherwise.
Example request
$ curl 'http://localhost:8080/api/statistics/v1/encap-client-versions/f68a6751-a800-4138-81a1-54efdc7af297' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response
HTTP/1.1 200 OK
X-Correlation-UUID: 8d59d65f-d9fa-4dc9-9c2a-b88135843ed6
Content-Type: application/json
Content-Length: 298
{
"uuid" : "f68a6751-a800-4138-81a1-54efdc7af297",
"status" : "READY",
"app_config_uuid" : "5819c469-ec0d-4757-bf9a-5498e609076d",
"last_used" : 365,
"generated_on" : "2025-10-28T13:49:57.584UTC",
"version_statistics" : [ {
"encap_client_version" : "3.9.0",
"count" : 10
} ]
}6. Callback
Encap supports two different service provider callbacks models, On-demand callback and Event callback. On-demand callback is requested for each activation or authentication operation, and provides a full response for the operation. Event callbacks are configured on the application configuration, and supports events for activation, authentication in addition to other events. The callback gives a status of the operation and a reference to the full response. Event callback is more resilient against event delivery issues and has a persistent event storage. It is possible to use both Event callback and On-demand callback in parallel.
6.1. On-demand callback
Callback for device activation and authentication, is used to inform the service provider about the status of a completed activation or authentication. The service provider can then wait for the callback instead of polling the server for status for the ongoing session.
6.1.1. Implementation
The callback endpoint must be implemented by the Service Provider and be reachable from the Encap server.
The endpoint needs to accept POST of the payloads described enrollment callback and here authentication callback.
The Encap server interprets any 2xx response as a success. Any other response will lead to a warning being logged in the server log, but this will have no effect on the status of the ongoing operation.
6.1.2. Usage
If the ´callback_address´ argument is set when creating the authentication object or enrollment, a callback will be sent by the Encap server to this address when the operation is completed (status is SUCCESS or FAILURE).
6.1.3. Important operational behaviour
The callback is performed asynchronously, so the client device will get an immediate response regardless of the availability of the service provider callback endpoint.
In order to monitor the health of the callback service, the operator needs to monitor (and act upon) Encap log messages with WARNING level for failing callbacks. Failure to do so will cause the device to think it is successfully activated or authenticated without the service provider being informed by of the result of the operation.
6.2. Event callback
Event callback reduces the need to poll for status changes. Event callback notifications are sent asynchronously to the service provider for selected events in Encap SCA. Events can also be filtered based on which API that initiated the operation.
6.2.1. Configuration
Event callback global properties
The encap-cluster.properties file contains parameters relevant for the configuration of the Event Callback feature. Cluster wide parameters for polling intervals, retries and timeouts can be configured to control the behaviour of the Event Callback service.
More details about the cluster configuration properties han be found in the Encap Server Administration Manual, chapter "Server config params".
Application configuration parameters
The application configuration parameter EVENT_CALLBACK_EVENTS is used to configure which events and APIs you want to trigger a callback. The EVENT_CALLBACK_URL parameter controls the URL for posting the event-callback objects.
This means that you can have a different set of events/APIs & URL per application config.
More details about the application configuration parameters.
Event types
| Event type | Description |
|---|---|
|
Device locked (status SUCCESS) |
|
Device unlocked (status SUCCESS) |
|
Device deactivated (status SUCCESS) |
|
Activation session has been completed (status SUCCESS or FAILURE) |
|
Authentication session has been completed (status SUCCESS or FAILURE) |
|
Recovery method has been added to the device (status SUCCESS) |
|
Recovery method has been removed from the device (status SUCCESS) |
|
Device recovery has been performed (status SUCCESS) |
Event APIs
| API type | Description |
|---|---|
|
Event for operations initiated by the mobile device |
|
Event for operations initiated from the REST API |
6.2.2. Event callback service provider API
Event callback API for notifying the service provider when events occur in Encap.
Encap server performs event-callback to service provider
POST /service-provider/event-callback-url
A http POST will be performed when the application configuration for the device has event callback configured
The event callback object
| Path | Type | Required | Description |
|---|---|---|---|
|
|
Yes |
Unique event ID. Can be used to identify duplicate callbacks for the same event (rare state) |
|
|
Yes |
The type of event that has occurred. See event-callback-events for possible values |
|
|
Yes |
The UUID of the owning app-config for this device |
|
|
Yes |
The UUID of the device that is affected by or has caused the event |
|
|
No |
The UUID of the session that this event belongs to (if any) |
|
|
Yes |
Status of the current event (SUCCESS or FAILURE) |
|
|
No |
Refers to details about the resource event (if available) |
|
|
Yes |
The request correlation ID from the request triggering this callback |
Example request body
{
"event_id" : "5018020e-43b4-41ad-a059-c9a35d724d49",
"subscribed_type" : "DEVICE_LOCKED",
"app_config_id" : "6f7eb0d0-345c-436c-a824-a039df7b5bb3",
"device_id" : "800e33c2-530a-499f-b3d1-ca0be243a725",
"session_id" : "83ab3f9d-2fc3-4b9d-b49e-1f682ac32416",
"ref" : "/devices/800e33c2-530a-499f-b3d1-ca0be243a725/lock",
"status" : "SUCCESS",
"request_correlation_id" : "9c868f02-bcc7-40cf-8c82-b7e3b67b78f5"
}Expected response from service provider
Return an empty response, with successful http code if the operation succeeds. Return a non 2xx http code object if something goes wrong.
Example request
$ curl 'http://localhost:8080/api/dummyspeventcallbackcontroller' -i -X POST \
-H 'Content-Type: application/json' \
-d '{
"event_id" : "5018020e-43b4-41ad-a059-c9a35d724d49",
"subscribed_type" : "DEVICE_LOCKED",
"app_config_id" : "6f7eb0d0-345c-436c-a824-a039df7b5bb3",
"device_id" : "800e33c2-530a-499f-b3d1-ca0be243a725",
"session_id" : "83ab3f9d-2fc3-4b9d-b49e-1f682ac32416",
"ref" : "/devices/800e33c2-530a-499f-b3d1-ca0be243a725/lock",
"status" : "SUCCESS",
"request_correlation_id" : "9c868f02-bcc7-40cf-8c82-b7e3b67b78f5"
}'Example response
HTTP/1.1 204 No Content6.2.3. Event callback status API
This provides a status overview of the event callback queues, including an availability-check of the event callback endpoint provided by the service provider. This will list the queue size for each app-config and perform an HTTP HEAD request towards the event callback endpoints configured.
Response objects types
Overall status object
| Field | Type | Description |
|---|---|---|
|
|
Overall queue health status |
|
|
List of event callback queues |
Queue details status object
| Field | Type | Description |
|---|---|---|
|
|
App-config id for the event callback queue |
|
|
Number of items in events callback queue |
|
|
Health status of the queue |
|
|
If 'status' is FAILURE, the error field should contain details about the failure |
Event-callback queue status
| Status | Description |
|---|---|
|
Queue health status is OK |
|
Queue status is unhealthy. An unreachable callback endpoint or a full callback queue will cause this error. |
Get API status
GET /api/admin/v1/status/callback
Example request
$ curl 'http://localhost:8080/api/admin/v1/status/callback' -i -u '5a1b356e-5c7c-40af-98d1-a7ac20787bfa:IWJLFRrczWIhLynsVtAq1g==' -X GETExample response - Status OK
HTTP/1.1 200 OK
X-Correlation-UUID: 103153e4-f4e4-4d99-b8b6-ee19b94dafc5
Content-Type: application/json
Content-Length: 137
{
"queues" : [ {
"id" : "87117a52-6f81-464f-a5d6-a5f1c13e1bb2",
"size" : 10,
"status" : "OK"
} ],
"status_all" : "OK"
}Example response - Status FAILURE
HTTP/1.1 200 OK
X-Correlation-UUID: ec437ef2-52fe-4fef-a7e0-91e2df432d9d
Content-Type: application/json
Content-Length: 259
{
"queues" : [ {
"id" : "2cd54132-1489-4119-8ee6-100959470ac5",
"size" : 10000,
"status" : "FAILURE",
"error" : "Queue size is larger than limit (5000) for app-config: 2cd54132-1489-4119-8ee6-100959470ac5"
} ],
"status_all" : "FAILURE"
}